Futures Slide As Renewed AI Disruption And Private Credit Fears Spark Selling
The rollercoaster continues: US equity futures are in the red again, trading near session lows, and set to extend Thursday's losses with as stocks underperform after yesterday's spectacular plunge in the momentum trade as NVDA's post record-breaking earnings/guidance plunge spooked markets that nothing is resolved about where AI goes next. As of 8:00am ET, S&P futures were down 0.6%, and set for a monthly loss after a whirlwind February marked by twin fears of a bubble in the AI trade and of the technology’s disruptive power. Nasdaq futures dropped 0.7%. In the latest AI contradiction, CoreWeave plunged 12% after data center operator reported a bigger-than-expected loss and higher capex fueling concern about overspending on infrastructure. But in a mirror image, Dell is 12% higher after its outlook for sales of AI servers exceeded estimates, a sign of robust demand for machines helping fuel the AI data center build-out. 10-year Treasury yields slid below 4%, while the USD is flat. Commodities are mixed, with Energy higher and Metals mixed (Silver outperforming vs Gold flat). Today's macro data focus is on PPI and Construction Spending.
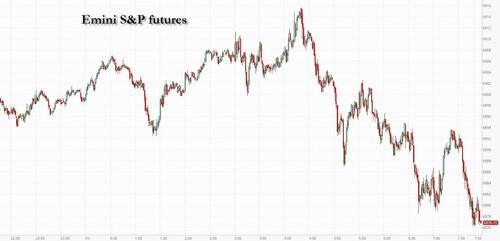
In premarket trading Mag 7 stocks are mixed: Nvidia is up 0.4% after sliding Thursday, other names are mostly lower (Alphabet little changed, Tesla -0.2%, Amazon -0.5%, Apple -0.5%, Meta Platforms -0.5%, Microsoft -0.8%).
- Block (XYZ) rallies 18% after the financial technology company said it was reducing its workforce by nearly half in a bet on AI. Jack Dorsey’s firm also raised its full-year outlook for gross profit, which was already above the average analyst estimate.
- CoreWeave (CRWV) slides 12% after the AI infrastructure software company reported a bigger-than-expected loss and boosted capital expenditures, spurring concerns about the company overspending on infrastructure.
- Flutter (FLUT) is down 15% after the gambling company reported fourth-quarter results that fell short of Wall Street estimates. Guidance for 2026 was worse than expected, according to analysts, who pointed to increasing competitive pressures in the US sports-betting market as a key concern.
- NCR Atleos (NATL) jumps 16% as The Brink’s Company said it will acquire the company in a cash and stock deal valued at about $6.6 billion.
- Netflix (NFLX) is up 8% after the streaming giant dropped out of the fight to buy Warner Bros. Discovery, effectively ending the bidding war for the Hollywood studio.
- Zscaler (ZS) is down 9% after the security software company’s second-quarter results weren’t seen as strong enough to reverse recent negative sentiment toward software companies.
In other corporate news, Netflix rose more than 7% after dropping out of the bidding for Warner Bros. Dell Technologies surged 11% following a strong sales forecast for its AI servers.
Nvidia suffered its worst day since April on Thursday, with the price action suggesting the world’s most valuable company is no longer being rewarded for spectacular results and remarkable guidance.
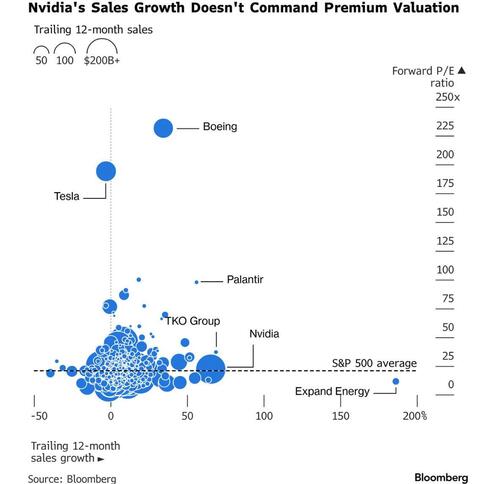
NVDA's plunge happens as the disruptive potential of AI has rattled US equities for weeks in what traders have dubbed the “AI scare trade.” The technology’s bellwethers have also lost momentum after powering S&P 500 gains for years, prompting investors to rotate into markets abroad and companies tied to broader economic growth.
“The outperformance highlights the possibility of a lingering overvaluation in some asset classes in the US, as well as doubts about the independence of the Federal Reserve’s future monetary policy,” said Guillermo Hernandez Sampere, head of trading at asset manager MPPM. “Barring an economic downturn in Europe, the outperformance should continue.”
“The outperformance highlights the possibility of a lingering overvaluation in some asset classes in the US, as well as doubts about the independence of the Federal Reserve’s future monetary policy,” said Guillermo Hernandez Sampere, head of trading at asset manager MPPM. “Barring an economic downturn in Europe, the outperformance should continue.”
As Wall Street tries to assess likely job losses at the hands of AI, Jack Dorsey’s financial technology firm Block is cutting 4,000 employees, nearly half its workforce, in a bet on AI changing the future of labor productivity. Then again, considering that Elon Musk fired 80% of Dorsey's last company before ChatGPT was even out - and it thrived - or that Block spent $68 million on a party a few months before the mass layoffs, suggests that the culprit here is bloat and terrible management, and not AI.
The market’s unease about private credit persists. In an rerun of the collapse of First Brands, a spectacular new private credit blowup in London has Wall Street chasing billions. And a private credit fund overseen by Apollo Global Management cut its dividend and marked down the value of its assets amid signs of strain in parts of its loan book.
Elsewhere, Anthropic, the AI start-up that has wiped billions off the market value of US stocks, remains in focus. US lawmakers, flummoxed by the Pentagon’s negotiating tactics, are warning that carrying out those threats would have significant consequences for the military ecosystem. Meanwhile, investment-grade bond markets, which had emerged as a safe haven during recent AI-driven swings in equities, are starting to show signs of strain.
US stocks saw inflows of $2.2 billion in the week ended Feb. 25, according to BofA citing EPFR Global data. Strategists led by Michael Hartnett see international stocks outperforming US for the rest of this decade.
"I don’t see any major correction coming, but any hint of a recession linked to AI in the US would certainly trigger some unpleasant trading,” said Andrea Tueni, head of sales trading at Saxo Banque France. “Europe is currently better positioned than the US and outperforming as its tech sector is much smaller and there is much less uncertainty on monetary policy.”
Earnings season wraps up next week, and has so far been somewhat disappointing, with the fewest S&P 500 companies beating estimates since 2022. Of the 481 to have reported so far, 73.4% have beaten forecasts, while nearly 22% have missed. No major US companies are expected to report on Friday, but Berkshire Hathaway’s annual report is due on Saturday, including Greg Abel’s first annual letter to shareholders on performance since taking over as CEO from Warren Buffett.
Europe’s Stoxx 600 was on track for an eighth straight monthly advance, its longest such streak in more than a decade; telecommunications and mining stocks lead gains, while travel and consumer products shares edged lower. Here are the biggest movers Friday:
- Deutsche Telekom shares rally while Vodafone dips following an El Español report that Telefonica is in talks over a potential acquisition of 1&1 in Germany
- Prysmian shares reverse earlier losses to trade as much as 2.3% higher following 4Q results from the Italian cable make
- Holcim gains as much as 1.5% after the French building materials firm reported fourth-quarter earnings that were slightly ahead of expectations and an outlook that is unlikely to trigger any major revisions to estimates, according to analysts
- Clariane shares jump 17%, the most since June, as analysts highlight improving margins and cost-saving initiatives at the French nursing home operator
- Saint-Gobain shares fall as much as 3.2%, the most since Jan. 13, after the French construction materials producer reported fourth-quarter results. Jefferies noted that like-for-like sales in the period trailed expectations
- Melrose Industries plunges as much as 16%, the biggest drop in almost a year, after earnings guidance from the aerospace business fell short of expectations, overshadowing a profit and cashflow beat delivered in 2025
- BASF shares fall as much as 5.4%, after the German chemicals company’s full-year results disappointed analysts, who expect consensus downgrades, even though a January pre-release had already revealed price and currency woes at the company
- Grifols shares declined as much as 8.3%, the most since April, after the Spanish company’s adjusted Ebitda for the fourth quarter missed estimates and it issued guidance that analysts say fell short of expectations
- Valeo falls as much as 4.9% following its results, despite guidance implying upgrades to consensus free cash expectations, after this metric also surprised to the upside in the second half of the year. Net income was, however, impacted by higher tax
- Wizz Air shares slid as much as 10%, the most since July, after shareholder Indigo Partners offered 10 million shares priced at £12.50, a discount of 6.4% to Thursday’s closing price
- Fugro shares fall as much as 12%, the most since September, after the Dutch geological data company saw its year-over-year adjusted Ebit plunge by 92% in what Jefferies says was a “challenging winter season”
Asian stocks traded mixed, with a key regional benchmark on track to close its best February on record as investors snapped up shares of the region’s AI infrastructure companies. The MSCI Asia Pacific Index gain as much as 0.6% Friday. South Korea’s Kospi fell 1%, as chipmakers Samsung and SK Hynix fell. Key gauges rose in Japan and Hong Kong, while Taiwan’s market was closed for a holiday. Asian stocks have been outperforming global peers, with the region’s hardware firms seen as beneficiaries of the AI buildout even as concerns grow over spending levels and business disruption. The MSCI regional gauge is up 6.7% this month, poised for the best February since it started trading in 1998. Chinese technology stocks in Hong Kong capped their worst month in two years, weighed by weak earnings and a lack of buying by mainland investors. Sentiment toward China’s Internet giants has cooled amid concerns over valuations and rising competition that’s eroding corporate bottom line. Meanwhile, global investors offloaded nearly $5 billion of South Korean equities on Friday, in a sign of profit taking after the equity benchmark rallied nearly 50% this year. The index rose past the 6,000 threshold this week, just a month after surpassing President Lee Jae Myung’s political goal of 5,000.
In FX, the dollar was set for a fourth straight monthly loss. The Norwegian Krone led G10 currencies with a +0.54% rise. The pound fell slightly against the dollar after a special election in the UK laid bare the unpopularity of Prime Minister Keir Starmer’s government.
In rates, treasuries extended gains, with the 10-year note on track for its best month in a year after yields have tumbled 26 basis points in February to 3.98%. Outperformance by front-end and belly steepened 2s10s spread by about 1bp, 5s30s by about 1.5bp. 10-year gilts and bunds are slightly cheaper vs US benchmark
In commodities, oil rose again, after sliding on Thursday. Gold traded flat, with prices headed for a seventh consecutive monthly advance.
The cross-asset moves reflect sustained demand for havens amid policy uncertainty from the Trump administration, tensions in the Middle East and questions about the strength of US economic growth. Swap traders added to bets on Federal Reserve interest-rate cuts, with a July move again almost fully priced after being briefly scaled back earlier this week.
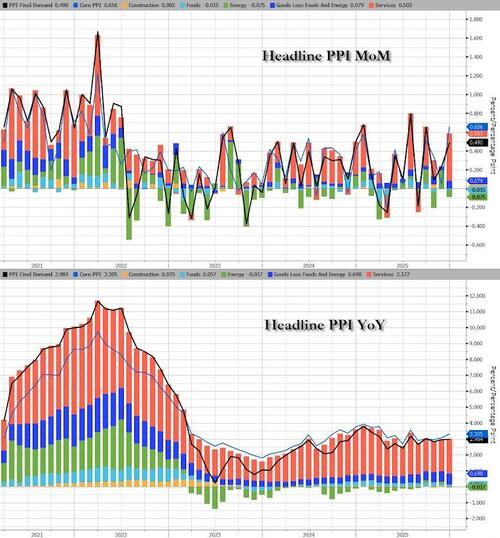
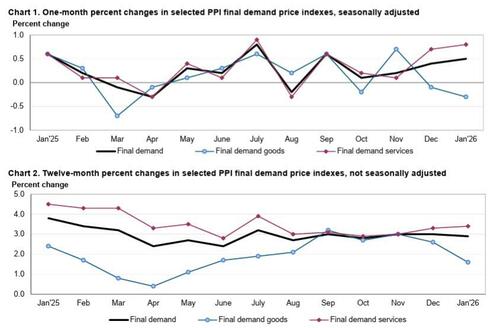
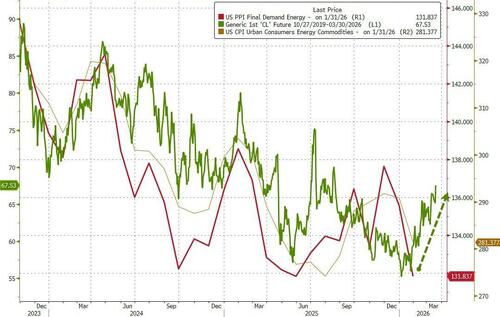
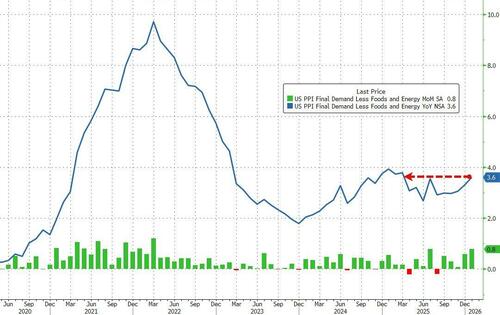
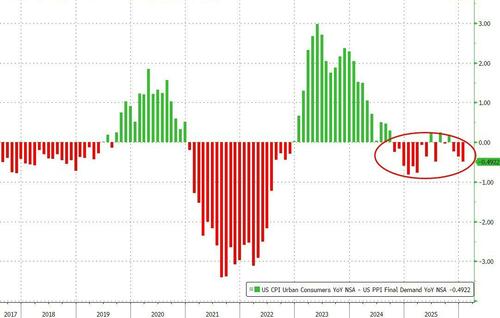
US economic data slate includes January PPI (8:30am), February MNI Chicago PMI (9:45am, several minutes earlier for subscribers), December construction spending (10am) and February Kansas City Fed services activity (11am). No Fed speakers are scheduled. Bloomberg Economics expects producer price inflation, which shows price trends before they reach consumers and feeds into the Fed’s preferred gauge of inflation, the personal consumption expenditures index, to have slowed to 0.2% in January from 0.5%. Potentially, that could bolster the case for further rate cuts.
Market Snapshot
- S&P 500 mini -0.3%
- Nasdaq 100 mini -0.3%
- Russell 2000 mini -0.8%
- Stoxx Europe 600 +0.2%
- DAX +0.2%
- CAC 40 -0.1%
- 10-year Treasury yield -1 basis point at 3.99%
- VIX +1.1 points at 19.74
- Bloomberg Dollar Index little changed at 1188.36
- euro little changed at $1.1801
- WTI crude +1.8% at $66.38/barrel
Top Overnight News
- The United States and Iran made progress in talks over Tehran's nuclear program on Thursday, mediator Oman said, but hours of negotiation ended with no sign of a breakthrough that could avert potential U.S. strikes amid a massive military buildup. RTRS
- Vice President JD Vance said Thursday that while military strikes against Iran remain under consideration by President Donald Trump, there is “no chance” that such strikes would result in the United States becoming involved in a years-long, drawn-out war. WSJ
- Anthropic rejected the Pentagon proposal to settle a dispute over terms for military use of its AI software. BBG
- A long-running conflict between Pakistan and Afghanistan’s Taliban regime has turned into what Pakistan declared Friday to be “open war,” with attacks reported in Kabul and along the neighbors’ shared border. WSJ
- China announced it would remove a reserve requirement for forward contracts selling the yuan in a move aimed at cooling the currency’s advance. The yuan snapped its longest winning streak since 2010. Still, options traders are betting on a stronger yuan. FT, BBG
- Inflation in Japan’s capital cooled below the central bank’s 2% target for the first time in over a year, but the slowdown is unlikely to derail further interest rate hikes. WSJ
- Mizuho Financial Group Inc. is planning to replace about 5,000 administrative jobs in Japan with artificial intelligence over the next 10 years, as the country’s third-largest lender tries to boost productivity. BBG
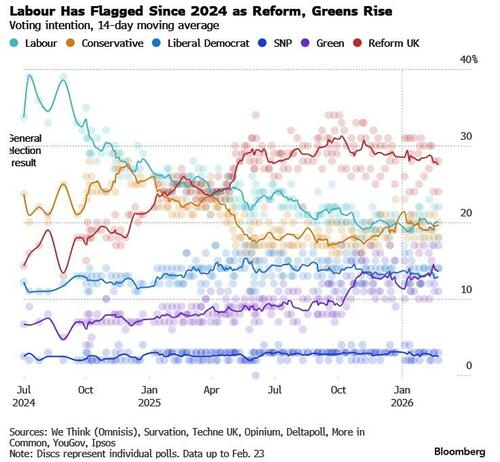
- The pound fell to its lowest level against the euro in more than two months as the Greens won a by-election in Manchester and Reform UK received the second-highest number of votes. The result underscored the threats facing PM Keir Starmer. BBG
- Netflix shares jumped premarket (NFLX +740bps premkt) after it dropped its bid for Warner Bros., clearing the way for Paramount’s $111 billion deal. The decision allows the streamer to focus on buybacks and its “build vs. buy” strategy. BBG
- IG bond markets are showing signs of stress, with spreads widening as investors grow wary of default risks in the software sector and pressure in private credit. Risk premiums, however, remain below long-term averages. BBG
Trade/Tariffs
- China's MOFCOM announces adjustments to anti-discrimination measures against Canada effective Mar 1st till Dec 31st 2026, will not impose relevant tariffs on some imports from China.
- Japan's PM Takaichi said US needs to honour its commitments on tariffs.
A more detailed look at global markets courtesy of Newsquawk
APAC stocks were ultimately higher heading into month-end but with price action choppy following the weak handover from the US, where sentiment was clouded by tech weakness, while participants also digested the recent US-Iran talks in Geneva. ASX 200 mildly gained as strength in tech and telecoms atoned for the losses in financials and consumer stocks. Nikkei 225 traded indecisively amid a firmer currency and a slew of mixed data releases from Japan, in which Industrial Production disappointed, Retail Sales topped forecasts, and Tokyo CPI printed firmer-than-expected but slowed across the board with the Core reading falling beneath the central bank's 2% price target for the first time since October 2024. Hang Seng and Shanghai Comp were varied with outperformance in Hong Kong as participants digested earnings releases from the likes of Baidu and Sun Hung Kai Properties, while the mainland initially lacked direction in the absence of fresh catalysts and ahead of next week's annual "two sessions", while Trump-Xi summit preparations were said to falter. However, late upside was seen after comments from China's Politburo meeting in which it stated that China's development process during the 14th Five-Year Plan is extraordinary and that it is necessary to continue to implement a more active fiscal policy and a moderately loose monetary policy.Top Asian News
Top Asian News
- China Politburo held a meeting on Friday and noted that China's development process during the 14th Five-Year Plan is extremely unusual and extraordinary. Said that it is necessary to continue to implement a more active fiscal policy and a moderately loose monetary policy. Necessary to focus on building a strong domestic market and step up the cultivation and expansion of new growth momentum.
European bourses (STOXX 600 +0.3%) are broadly firmer, with the SMI (+0.7%) the clear outperformer after Swiss Re (+3.6%) posted a 47% Y/Y rise in 2025 net profit while announcing a USD 500mln share buyback. Lagging behind its peers is the CAC 40 (-0.1%), with very company-specific news to drive the index. European sectors are mixed. Telecommunications (+1.3%) outperform after Spain's Cellnex (+0.6%) saw 2025 operating profit rise more than double annually and Telefonica (+3.7%) reportedly negotiating the purchase of 1&1 (+9.4%)in Germany in a EUR 5bln deal. On the flip side, Travel and Leisure (-1.8%) is underperforming despite positive IAG (-5.5%) earnings, in which the Co. beat FY profit expectations and announced a EUR 1.5bln share buyback.
Top European News
- UK former Deputy PM Rayner noted the Gorton and Denton by-election results are a "wake up call" and Labour "has to be braver"; Sky News suggests these remarks will be taken as a direct aim at UK PM Starmer and his leadership.
- EU Commission eyes a legal loophole to bypass Hungary's veto of a EUR 90bln euro loan, according to FT.
- UK Green Party wins parliamentary seat in Gorton and Denton, defeating UK PM Starmer's Labour in the by-election.
FX
- DXY is choppy but ultimately slightly softer following subdued APAC trade amid mixed sentiment, whilst the tone in Europe is tentative. Modest downticks in the index were seen as the EUR strengthened following the hotter-than-expected French CPI data (more below). Aside from that, newsflow in the European morning has been on the quieter side as USD traders gear up for US PPI data later in the session. DXY resides in a current 97.611-97.824 range at the time of writing, within Thursday’s 97.489-97.984 parameter.
- EUR/USD eked mild gains after oscillating around the 1.1800 focal point overnight, with a more convincing move above the level seen after the hotter-than-expected French and Spanish Prelim CPI metrics. EUR/USD resides in a 1.1789-1.1822 range awaiting the German Prelim CPI later today. The single currency then slipped to the unchanged mark after German state CPI metrics, where the Y/Y metrics generally showed a bit more cooling than what is forecasted for the mainland.
- GBP/USD languished near the 1.3500 level following the prior day's underperformance owing to credit concerns, and with overnight price action contained after UK GfK consumer confidence fell to its lowest level that was last seen in November. Overnight, UK journalists focused on the Gorton and Denton by-elections in which the Green party won, with Reform second and Labour third. With Labour losing a seat they held for almost 100 years, UK PM Starmer's leadership could be at risk. Nonetheless, GBP/USD saw little reaction to the results announcement, and currently resides in a 1.3461-1.3507 range, after finding support at its 200 DMA (1.3442) yesterday. Ahead, BoE’s Chief Economist Pill is due to give some remarks.
- USD/JPY retreated amid the early subdued risk appetite and following a slew of data, including Tokyo CPI, which printed firmer-than-expected across the board, but slowed from the previous with Core inflation back beneath the BoJ's price goal. The pair pared back some losses as the DXY recouped some overnight losses. USD/JPY trades in a 155.54-156.12 range vs yesterday’s 155.70-156.43 parameter.
- Antipodeans rebounded from the prior day's trough and narrowly outperform in the European morning, but with further upside contained by the mixed risk appetite and amid a weaker CNH, which was pressured after the PBoC actions to slow currency appreciation, in which it cut the FX risk reserve ratio to 0% and set a weaker-than-expected CNY fix by maintaining it at the prior day's level.
Fixed Income
- USTs are firmer by a handful of ticks this morning, and trades within a 113-16 to 113-19 range. Really not much driving things for the US paper this morning, and remains towards the prior day’s peaks. The upside in USTs on Thursday was facilitated by subdued risk appetite and a decent 7yr auction. Focus remains on the geopolitical situation, following US-Iran talks. Meetings have concluded, and whilst there have reportedly been some positive developments, uncertainty remains. Reports suggest that US President Trump is expected to convene senior advisers on Friday for detailed discussions on Iran and to decide on a course of action toward Tehran. Internal deliberations are said to be focused not on whether a strike would occur but on its scope and potential targets. Next up, US PPI.
- Bunds are incrementally firmer/flat, and currently reside within a 129.76 to 129.99 range. Initially held towards recent highs, but has since slipped towards the unchanged mark following the hotter-than-expected French/Spanish inflation metrics. Though the German State CPIs thereafter spurred some modest upticks in Bunds, given the Y/Y metrics generally showed a bit more cooling than what is forecasted for the mainland.
- Gilts are firmer by around 10 ticks, to currently trade near the upper end of a 93.00-93.30 range. Overnight, UK journalists focused on the Gorton and Denton by-elections in which the Green party won, with Reform second and Labour third. With Labour losing a seat they held for almost 100 years, UK PM Starmer's leadership could be at risk – which in theory would place pressure on UK-assets. This has not been reflected in price action this morning, though analysts at GS opined that the risk had already been priced in by markets.
- Japan sold JPY 2.15tln in 2-year JGBs; b/c 3.32x (prev. 3.88x); average yield 1.244% (prev. 1.253%).
- Australia sold AUD 800mln 2.75% November 2028 bonds, b/c 3.86, avg. yield 4.1849%.
Commodities
- WTI Apr’26 and Brent May’26 futures are firmer within USD 64.85-65.90/bbl and USD 70.42-71.49/bbl intraday ranges thus far, respectively. Gains follow yesterday’s US-Iran negotiations, which ultimately failed to reach an accord, but the sides agreed to continue technical talks. Mediators reported "unprecedented openness to new and creative ideas". Both sides reportedly moved closer on specific elements of an agreement related to nuclear limits and sanctions relief. That being said, major sticking points remain.
- Spot gold trades within a narrow range after only modestly gaining on yesterday’s US-Iran saga, which ended in no deal, but talks are poised to continue next week. Traders will be focused on any potential US military action this weekend in a bid to pressure Iran. Spot gold resides tight USD 5,167-5,200.64/oz range at the time of writing. Spot silver is firmer by some 1.5% intraday but contained to within Wednesday’s ranges.
- Base metals are firmer across the board despite the choppy risk tone in Asia, but prices are underpinned by the softer USD. Some desks attribute the rise to the stalled US-Iran talks and strengthening demand signals from China. The upside also comes ahead of next week’s China “Two Sessions”, where formal approval of the 15th Five-Year Plan and new stimulus measures for infrastructure and technology (AI, EVs, grid networks) are anticipated. 3M LME copper resides in a USD 13,243.73-13,508.13/t.
- London Metal Exchange announces the consultation for introducing regulatory position limits, exemptions and position management controls.
- Iron ore port stockpiles hit record levels in China as mines continue to add supply.
- Abu Dhabi reportedly offers more oil to partners, heading into the OPEC+ meeting, Bloomberg sources say.
- India is reportedly looking to cut coal imports for power plants at least 30% this year, sources say.
- China SHFE warehouses weekly changes: Copper +43.7%, Aluminium +19.7%, Zinc +44.9%.
- A local ceasefire has been established near the Zaporizhzhia nuclear power plant, TASS reported. Further by RIA stating one power line is being repaired at the power plant.
Geopolitics: Middle East
- US authorises the departure of some embassy personnel and families from Israel amid safety risks.
- Iran urges US to abandon "excessive demands" to reach deal, Sky News Arabia reported citing AFP.
- Iranian spokesperson said "In the event of any conflict, American soldiers and their equipment will be destroyed, and all US resources and interests in the region will be within the range of Iranian forces", via Iran International.
- Top Middle East commander briefed US President Trump on military options on Iran, according to ABC News.
- US VP Vance said negotiations depend on what the Iranians do and there is no chance that any potential strikes on Iran will result in engaging in a war for years.
- US President Trump is expected to convene senior advisers on Friday for detailed discussions on Iran and to decide on a course of action toward Tehran, according to Israel Hayom citing US officials. Internal deliberations are said to be focused not on whether a strike would occur but on its scope and potential targets, while options under discussion include nuclear facilities, missile sites, state institutions and infrastructure.
- Iranian Foreign Minister said further progress has been made in our diplomatic engagement with the US, also said mission of the technical teams is as important as our mission.
- Oman's Foreign Minister is scheduled to meet with US VP Vance and other US officials in Washington on Friday.
Geopolitics: Others
- China said it is not possible to join denuclearisation talks at this stage.
- AFP reported of clashes near a major border crossing between Afghanistan and Pakistan.
- Afghan Ministry of Defence said their military operation resulted in casualties among Pakistani forces and came in defence of their territory and people, while it vowed to respond to future attacks.
- Loud explosion heard in Afghanistan's capital of Kabul and Pakistani fighter jets are reportedly conducting a raid on Kabul.
US Event Calendar
DB's Jim Reid concludes the overnight wrap
d
Tyler Durden
Fri, 02/27/2026 - 08:30


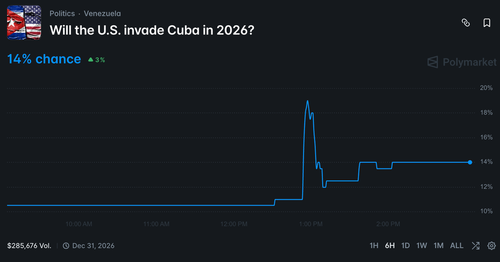
 Source:
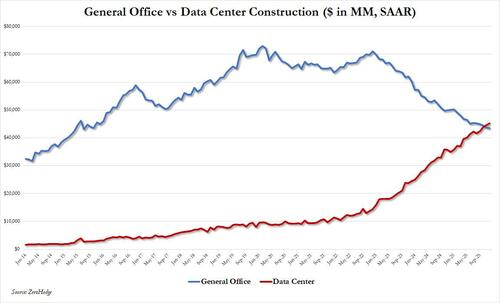
Source: 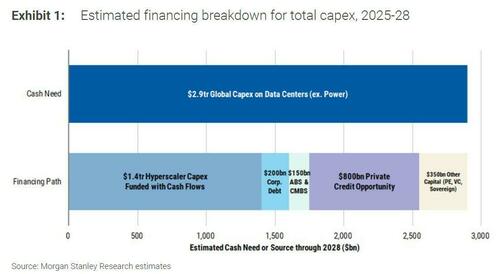


 Taliban near the Torkham border, via AFP.
Taliban near the Torkham border, via AFP.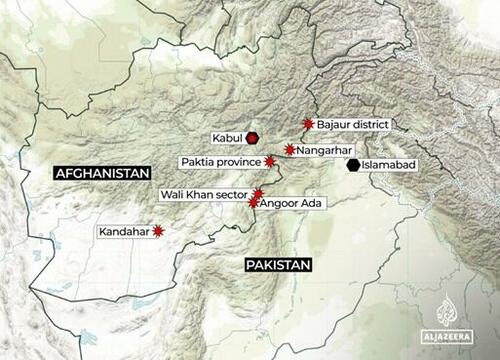 via Al Jazeera
via Al Jazeera



 via AFP
via AFP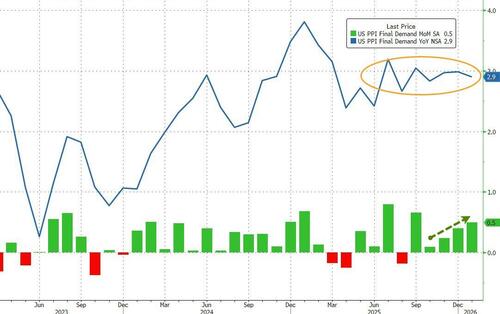





Recent comments