The Ellisons Taking Over Warner is Pants on Fire Stuff, but Team Progressive Just Whines
The post The Ellisons Taking Over Warner is Pants on Fire Stuff, but Team Progressive Just Whines appeared first on CEPR.
Speak Your Mind 2 Cents at a Time
The post The Ellisons Taking Over Warner is Pants on Fire Stuff, but Team Progressive Just Whines appeared first on CEPR.
Authored by Steve Watson via Modernity.news,
A new advertisement from conservative group American Sovereignty hammers Democrats for staying seated during President Trump’s State of the Union call to prioritize American citizens over illegal aliens, using footage that lays bare their priorities.
The ad, which dropped Thursday, features Trump stating, “If you agree with this statement, then stand up and show your support: The first duty of the American government is to protect American citizens, not illegal aliens.”
Republicans rose in applause while Democrats remained glued to their seats, with overlays labeling the divide and accusing Dems of siding with “illegal immigrant criminals.”
The spot cuts to Trump’s “These people are crazy” remark before closing with “Republicans are for you.”
As we highlighted in previous coverage, Democrats’ behavior during the SOTU revealed whose side they’re on—and it’s not the American people.
Many boycotted the event or sat through applause for victims of illegal alien crime, exposing their allegiance to open borders over citizen safety.
They doubled down afterward, with figures like Debbie Wasserman Schultz labeling the speech “absolutely revolting” for prioritizing Americans.
Even more telling, Rep. Rashida Tlaib appeared to chant “KKK” while Republicans chanted “USA!”—a moment ripe for its own ad.
The ad’s release comes as Republicans eye midterms, with a GOP spokesperson telling the Washington Examiner that vulnerable House Democrats should “get comfortable re-watching the moment they revealed they’re nothing more than America-hating scums who stayed glued to their seats.”
The Democrats handed Republicans a raft of campaign material just in time for the midterms. They don’t even try to hide their hate for Americans
If they can’t stand for ‘protect Americans first,’ what exactly are they standing for?
This ad marks the first in a seven-figure blitz targeting battleground states like North Carolina, Michigan, and Georgia, per Politico, aiming to leverage the SOTU optics for electoral gains.
Trump himself called out Democrats during the speech, saying “you should be ashamed of yourself” for not standing, a moment echoed in White House criticisms and conservative commentary.
As midterms loom, this footage serves as a stark reminder: Democrats’ refusal to stand for American priorities hands Republicans ammunition to rally voters against policies that put citizens last.
Your support is crucial in helping us defeat mass censorship. Please consider donating via Locals or check out our unique merch. Follow us on X @ModernityNews.
Tyler Durden Fri, 02/27/2026 - 11:45Overnight, Pakistan launched airstrikes across Afghanistan, including targets in the capital of Kabul, soon after which Pakistan's Defense Minister Khawaja Asif by Friday morning declared an "all-out war" between the two countries.
Hours prior to the commencement of airstrikes and heavier clashes, Afghan Taliban forces reportedly attacked Pakistani border troops Thursday night in retaliation for Pakistani airstrikes earlier in the week.
A Pakistani military spokesman has said that 274 Taliban fighters have been killed and more than 400 injured by Pakistani strikes, adding that 74 Taliban posts were destroyed and 18 captured - and counting.
 Taliban near the Torkham border, via AFP.
Taliban near the Torkham border, via AFP.
The Taliban for its part has said that 55 Pakistani soldiers were killed and 19 posts seized. Kabul have acknowledged Taliban fighters killed, 11 wounded, and 13 civilians injured in the mountainous northwest border region where the line of fighting is concentrated.
Since the Taliban returned to power in 2021, relations between Afghanistan and Pakistan, which share the disputed 1,600-mile Durand Line, have shifted from cautious engagement to open hostility. The history has been marked by shifting from one-time allies to on-and-off again enemies. Many analysts are pointing to 'blowback' for Pakistan after sponsoring the Taliban's rise in the first place, decades ago (which also had the help of the CIA in 'Operation Cyclone').
Islamabad accuses Afghanistan of sheltering Tehrik-i-Taliban Pakistan (TTP) militants who carry out cross-border attacks.
Analysts say the latest escalation marks the first time Pakistan has directly targeted Taliban government sites, or essentially going all out against Kabul, rather than limiting strikes to alleged TTP positions.
Pakistan has said its forces have taken out a number of tanks and armored vehicles, as well as artillery positions. The Taliban relies on equipment left behind and confiscated after US and NATO forces rapidly withdrew from the country in the summer of 2021.
Pakistan has struck Kabul and declared it’s in an ‘open war’ with Afghanistan, after Islamabad accused the Afghan Taliban of opening fire along the shared border.
— Al Jazeera English (@AJEnglish) February 27, 2026
The fighting follows days of hostilities, despite a ceasefire agreement in October. pic.twitter.com/uQO1NT4H9f
It remains that Pakistan's army has total force domination; however, the Taliban can still inflict pain through acts of terrorism, which Pakistani cities have suffered immensely under.
Acts of terror by Islamist groups have become almost a regular occurrence in Pakistan - with many suspected of having support through Afghanistan. For example, we reported on this major incident just weeks ago as follows:
At least 31 people were killed and 169 others injured on Friday when a suicide bomber struck a Shia mosque on the outskirts of Islamabad during Friday prayers, Pakistani officials said, in one of the capital’s deadliest attacks in over a decade.
The blast happened in the Khadija al-Kubra Imambargah mosque in the outskirts of Islamabad, with police saying the attacker had been stopped at the mosque gate before opening fire and setting off explosives among worshipers, according to officials cited by Reuters.
As for how the warring sides compare, regional publication Al-Monitor lays out the following:
Pakistan's armed forces benefit from good recruitment and retention, bolstered by equipment from its main defense partner China. Islamabad continues to invest in its military nuclear programs and is also modernizing its navy and air force...
Pakistan has 660,000 active personnel in its defense forces, of whom 560,000 are in the army, 70,000 are in the air force, and 30,000 are in the navy.
The strength of the Afghan Taliban's military is thinner, with only 172,000 active personnel. The group has, however, announced plans to expand its armed forces to 200,000 personnel.
The Taliban's international isolation has meant that it cannot modernize its military - but still, there have been reports of drone usage against Pakistan positions.
As is typical, Pakistan points the finger at Israel and India for fomenting instability in the region:
“I think we must not miss out at this point the timing of this attack by Afghanistan. If you look at the visit of Indian PM Narendra Modi to Israel, it will be easier for you to connect the dots and understand that who is behind these attacks.” – Foreign affairs expert Dr Hassan… pic.twitter.com/uGjwMADETA
— Pakistan TV (@PakTVGlobal) February 27, 2026
Taliban authorities said their forces carried out drone strikes against military targets inside Pakistan as clashes between the two countries continued, according to statements from the defense ministry and a government spokesperson on Friday.
Pakistan’s Information Minister Attaullah Tarar said Pakistani Taliban militants attempted to deploy drones against targets within Pakistan, but air defense systems intercepted them and no casualties were reported.
 via Al Jazeera
via Al Jazeera
Overall, Pakistan is experiencing some serious blowback for its years-long policies... Sky News' Yalda Hakim points out that "Pakistan spent decades backing and sheltering the Afghan Taliban - its defense minister acknowledged that to me on camera. Now it says Taliban-ruled Afghanistan is providing sanctuary to militants attacking Pakistan. The consequences are unfolding in real time."
Tyler Durden Fri, 02/27/2026 - 11:25Authored by Naveen Athrappully via The Epoch Times,
The federal government has filed lawsuits against five states—Utah, Oklahoma, Kentucky, West Virginia, and New Jersey—accusing local officials of failing to provide full voter registration lists as requested, the Department of Justice (DOJ) said in a Feb. 26 statement.
“The Attorney General is uniquely charged by Congress with broad authority to request election records under the Civil Rights Act of 1960,” the DOJ said. “This Act allows her to demand the production, inspection, and analysis of statewide voter registration lists that can be cross-checked effectively for improper registrations.”
However, the states have failed to produce voter rolls requested by the attorney general, according to the complaints.
The Justice Department’s Civil Rights Division has now filed complaints against 29 states and the District of Columbia over the issue.
The lawsuit against Utah argued that the attorney general sent a letter seeking the state’s computerized statewide voter registration list on July 15. The state did provide the information on July 31, but this was the publicly available redacted version of the list.
On Aug. 14, the attorney general sent another letter, demanding that Utah provide a current, unredacted, electronic copy, the lawsuit said.
The state subsequently raised privacy concerns related to the demand for federal election records, and has yet to provide the full list as requested.
Multiple laws require state officials and election officers to maintain and preserve records relating to voter registrations and related actions. The lawsuit accused Utah’s chief election officer of violating the Civil Rights Act, the complaint said.
Similar allegations were made in lawsuits against officials from Oklahoma, Kentucky, West Virginia, and New Jersey.
“Accurate, well-maintained voter rolls are a requisite for the election integrity that the American people deserve,” Attorney General Pamela Bondi said. “This latest series of litigation underscores that this Department of Justice is fulfilling its duty to ensure transparency, voter roll maintenance, and secure elections across the country.”
Assistant Attorney General Harmeet K. Dhillon of the Civil Rights Division said that many state election officials are fighting them in court “rather than show their work.”
“We will not be deterred, regardless of party affiliation, from carrying out critical election integrity legal duties,” Dhillon said.
The Epoch Times reached out to officials from the five states for comments and did not receive a response by publication time.
On Sept. 16, the DOJ sued Oregon and Maine, accusing them of failing to provide voter registration rolls. The same month, similar complaints were filed against California, Michigan, Minnesota, New York, New Hampshire, and Pennsylvania.
In December, the DOJ filed lawsuits against Delaware, Maryland, New Mexico, Rhode Island, Vermont, Washington, Georgia, Illinois, Wisconsin, and the District of Columbia. Last month, Arizona and Connecticut were sued by the department.
Following Bondi’s letter requesting Minnesota provide access to the state’s voter rolls, Minnesota Secretary of State Steve Simon said in response on Jan. 25: “The answer to Attorney General Bondi’s request is no. Her letter is an outrageous attempt to coerce Minnesota into giving the federal government private data on millions of U.S. Citizens in violation of state and federal law. This comes after repeated and failed attempts by the DOJ to pressure my office into providing the same data.”
Simon said that Minnesota’s elections were “fair, accurate, honest, and secure,” and that “the law does not give the federal government the authority to obtain this private data,” such as Social Security and driver’s license information.
Election IntegrityThe Justice Department’s attempt to secure full voter rolls from states follows President Donald Trump’s March 2025 executive order “Preserving and Protecting the Integrity of American Elections,” which required the attorney general to prioritize the enforcement of laws restricting voter registration and voting by noncitizens.
Republicans are also pushing forward the SAVE America Act, which requires Americans to prove their citizenship when registering to vote. It also mandates that citizens show photo identification when casting ballots, or include a photocopy of their identification when voting by mail.
The bill passed the House of Representatives on Feb. 11 but faces an uncertain future in the Senate.
Democrats have opposed the measure, with Senate Minority Leader Chuck Schumer (D-N.Y.) saying that the bill was “dead on arrival” in the chamber.
“The goal of the SAVE Act is the same: disenfranchising American citizens and making it harder for eligible people to vote, particularly low-income Americans and people of color,” Schumer said on the Senate floor on Feb. 9.
Earlier this month, Sen. Alex Padilla (D-Calif.) criticized the SAVE Act, saying that it would do more harm than good, according to a Feb. 2 statement from the lawmaker’s office.
“Voting by noncitizens in federal elections is already a felony and it is extremely, extremely rare. This bill does nothing to secure our elections while seeking to disenfranchise millions of married women, military members and spouses, and rural, low-income, and minority voters,” Padilla said.
Several progressive and left-wing groups have opposed the voter ID requirements, including the League of Women Voters, the American Civil Liberties Union, and the Brennan Center for Justice.
Meanwhile, Trump said in a Truth Social post on Feb. 13 that he plans to sign an executive order mandating voter ID for the midterm elections if the SAVE Act is not passed by the Senate.
“We cannot let the Democrats get away with NO VOTER I.D. any longer,” the president wrote.
“This is an issue that must be fought, and must be fought, NOW! If we can’t get it through Congress, there are Legal reasons why this SCAM is not permitted,” he said. “I will be presenting them shortly, in the form of an Executive Order.”
Tyler Durden Fri, 02/27/2026 - 11:05Authored by Ben Cline via RealClearPolitics,
Once you burn your credibility, it’s hard to get back.
Virginia Gov. Abigail Spanberger deceived voters and concealed her true leftist agenda to win the Governor’s Mansion last year. Now she and her fellow Democrats are lying to Virginians about a new gerrymandered congressional district map they placed on the ballot as a constitutional amendment on April 21.
It’s a naked attempt to make it impossible for Republicans to win election to Congress in most places in Virginia, and it’s why she was rewarded with the plum assignment of responding to President Trump’s State of the Union address this week.
The Virginia Supreme Court has already had one chance to stop the gerrymandering by upholding a judge’s ruling that Democrats cut legal corners to get the measure on the ballot. The justices, however, inexplicably chose to wait until the vote happens.
I filed another lawsuit to bring new challenges, along with my colleague, Rep. Morgan Griffith (VA-9), and the RNC and NRCC. We won in circuit court, blocking the referendum again, so our Supreme Court will have another chance to do the right thing.
As we wait for a ruling, it’s important that people have the facts.
Spanberger masqueraded as a moderate in her campaign and won ceaseless praise from the media for her focus on “affordability.” But she dropped that as soon as she was sworn in and went right back to what she truly believes.
She returned Virginia to the multi-state, radical environmental scheme that artificially raises electricity rates by $500 million every year. She’s currently considering a variety of tax increases proposed by Democrats in the Virginia legislature, including bumps in the sales and income tax, as well as taxes on everyday services like dog walking and gym memberships. She has yet to rule out raising taxes on anything.
All of this is the opposite of what she ran on.
Now Gov. Spanberger and her Democrats have turned to stealing congressional seats.
And naturally, they’re lying about that as well.
It’s nothing complicated. They’re taking Virginia’s current congressional district map, which produced six Democrats and five Republican members, and redrawing the lines to twist it into a 10-to-1 map in favor of Democrats.
Kamala Harris won here in the 2024 presidential race with less than 52% of the vote, but this map would award her party 91% of our congressional seats.
They’re assigning new federal representation to Virginians who didn’t ask for it, and there’s every likelihood that some of the lines were drawn to benefit specific Democrat politicians. One thing that’s certain is that no one was thinking of the well-being of voters when they hatched this plot.
As an example, take Fairfax County, vote-rich and dominated by Democrats in Northern Virginia outside Washington, D.C.
The new map carves Fairfax into five pieces and attaches them to districts that reach deep into Virginia’s rural regions. Picture the county as an octopus that has tentacles running throughout the state, and you’ll have an idea.
The configuration ensures that most rural voters will be represented by people who live in Fairfax and were elected by voters in the D.C. suburbs. It’s difficult to imagine what these groups might have in common geographically, culturally, or economically.
To top it off, just a few days ago, Democrats in the General Assembly decided that they hadn’t cheated enough and twisted the screws even more to guarantee total victory in 10 of the 11 districts.
States usually redistrict following a census, but Democrats claim they must act now to balance Republican activities in other states. This excuse falls apart because most observers agree that Virginia’s new map is a particularly egregious example of partisan gerrymandering.
And Democrats lie when they talk about it.
The party that told us that Joe Biden was mentally sharp now wants us to think a 10-to-1 congressional map promotes “fair elections,” as their advertising claims.
They were even dishonest in the ballot question they wrote, which says it will temporarily “restore fairness” – without explanation or context – to elections in Virginia until the regular redistricting occurs in 2030.
We shouldn’t let politicians select their own voters, and Virginians were wise enough to see this coming.
Just six years ago, a whopping 66% of voters approved a constitutional amendment creating an independent redistricting commission to remove map-drawing from partisans. Unable to resist the lure of unchecked power, Virginia Democrats are trying to trick voters into undoing that so they can burgle those congressional seats.
National Democrats are paying attention.
House Minority Leader Rep. Hakeem Jeffries (D-NY) has already sent $5 million to the campaign to support the new map and pledged to spend “whatever it takes” on top of that.
Democrats hilariously claim to be restoring fairness.
But a party powerful enough to ram this down everyone’s throat isn’t the victim of unfairness. It’s the cause of it.
Rep. Ben Cline, a Republican, represents Virginia’s 6th District in the U.S. House of Representatives.
Tyler Durden Fri, 02/27/2026 - 10:35Former Special Counsel Jack Smith has long operated under Oscar Wilde’s rule that “the only way to get rid of a temptation is to yield to it.”
Over the last few months, the public has learned of a wide array of secret orders targeting members of Congress, Trump allies, and others.
Now, the Administration has learned that FBI Director Kash Patel and White House Susie Wiles were also targeted by Smith in 2022 and 2023 when they were private citizens.
Smith was a controversial choice as Special Counsel because of his history of excessive legal arguments and tactics, including his unanimous loss before the Supreme Court in tossing out the conviction of former Virginia Governor Robert McDonnell.
His tendency to stretch the law to the breaking point also did not play well with juries in high-profile cases, as in his case against John Edwards, which ended in acquittal.
Despite such criticisms, Smith immediately returned to his past pattern of tossing aside any restraint or caution. Even Democrats this year expressed objections to his targeting of Republican members of Congress, including former House Speaker Kevin McCarthy.
Smith told carriers not to tell members of Congress that their calls were being seized. Not only did such records reveal potentially confidential sources, ranging from journalists to whistleblowers, but Smith’s gag order prevented Congress from responding to check the abusive demand.
Now, the Administration is alleging that Smith and the prior Administration effectively buried the targeting of Patel and Wiles. It took a year into the new Administration for these orders to be uncovered.
The early accounts of the orders contained equally disturbed elements. Reuters reported that “in 2023, the FBI recorded a phone call between Wiles and her attorney, according to two FBI officials. Wiles’ attorney was aware that the call was being recorded, and consented to it, but Susie Wiles was not.”
It is astonishing to hear of a lawyer agreeing to the FBI recording of an attorney-client meeting as a general matter.
However, to do so without informing your counsel would be a breathtaking invasion of such protected communications.
There is much we still do not know.
On its face, these orders appear consistent with the earlier abusive demands. Smith had virtually no basis for targeting Republican members and Trump allies. It was a fishing expedition in which Smith simply compiled lists of every well-known ally of President Trump.
There are also concerns over the response to this controversy. There are reports of 10 FBI employees being fired. Agents often carry out the orders of superiors in such investigations. The Administration should assure the public that these agents were afforded due process before being ousted due to their work on orders.
The recently disclosed files from these investigations are an indictment of Smith himself. He was given a historic mandate to investigate a former president. Rather than exercise a modicum of restraint to show the public that this was not a partisan effort, Smith yielded to his worst temptations in targeting a long list of Republicans.
In his prior testimony, Smith offered little to justify these orders beyond a shrug that such secret orders routinely occur. However, he was targeting a “who’s who” listing of top political opponents to President Biden and the Democrats.
To make matters worse, Smith struggled to release damaging information (and even schedule a trial) on the very eve of the 2024 presidential election. Every action that Smith took only magnified his agenda to influence the election. He became a prosecutor consumed by his antagonism toward Trump and his unchecked power.
Nothing was sacred for Smith. His demands in the investigation from the courts included a wholesale attack on free speech values.
Ultimately, these files are not only an indictment of Jack Smith but also of former Attorney General Merrick Garland, who failed to exercise his authority to oversee Smith and protect core constitutional values.
It is essential that Congress and the Administration fully investigate Smith’s surveillance demands. Smith has long demanded accountability for others while evading such accountability for his own actions.
If past orders are any indication, the Patel and Wiles orders were likely based on sweeping generalities and demands for absolute secrecy. That is the signature of Jack Smith. Indeed, Smith appears to have replicated his increasingly infamous record with the collapse of two high-profile cases and lingering questions over his judgment and actions.
He has again yielded to his temptations, and the public has paid the price.
Jonathan Turley is a law professor and the author of the New York Times bestselling “Rage and the Republic: The Unfinished Story of the American Revolution.”
Tyler Durden Fri, 02/27/2026 - 09:40OpenAI has closed a new funding round that could total $110 billion, valuing the ChatGPT maker at $730 billion pre-money and potentially putting it on course for an IPO in the second half of the year, according to a new Financial Times report.
The three investors in the deal are Nvidia, Amazon, and SoftBank. People familiar with the deal say this opens the pathway to the public markets at the end of this year.
Breaking down funding numbers by strategic investors:
Amazon: $15 billion upfront, plus $35 billion later if OpenAI goes public or achieves AGI
Nvidia: $30 billion
SoftBank: $30 billion
Another $10 billion may come from sovereign wealth funds and other investors
The FT noted that the new funding round comes on top of the $40 billion already on OpenAI's balance sheet, giving the company more runway to rapidly expand and develop new models and AI infrastructure. OpenAI expects to remain unprofitable until 2030, when management forecasts it will turn free cash flow positive.
In a separate release, Amazon detailed its major multi-year partnership with OpenAI, centered on enterprise AI infrastructure, distribution, and custom model development.
Here are the highlights of the Amazon-OpenAI investment:
Amazon will invest $50 billion in OpenAI, with $15 billion upfront and another $35 billion later if certain conditions are met.
AWS and OpenAI will jointly build a "Stateful Runtime Environment" powered by OpenAI models and offered through Amazon Bedrock, aimed at helping customers run AI apps and agents with persistent context, memory, tool access, and compute.
AWS becomes the exclusive third-party cloud distribution provider for OpenAI Frontier, OpenAI's enterprise platform for building and managing teams of AI agents.
OpenAI will expand its AWS infrastructure commitment by $100 billion over 8 years, on top of an existing $38 billion agreement.
As part of that, OpenAI will use roughly 2 gigawatts of AWS Trainium capacity, spanning Trainium3 and future Trainium4 chips, to support Frontier, Stateful Runtime, and other advanced workloads.
OpenAI and Amazon will also develop custom OpenAI-based models for Amazon's customer-facing apps, giving Amazon teams another model option alongside its in-house Nova family.
"OpenAI and Amazon share a belief that AI should show up in ways that are practical and genuinely useful for people," OpenAI boss Sam Altman stated, adding, "Combining OpenAI's models with Amazon's infrastructure and global reach helps us put powerful AI into the hands of businesses and users at real scale."
Altman commented on today's announcement, saying, "As long as revenue keeps growing, the deals are not circular."
Well...
"As long as new investors keep coming, the Ponzi scheme won't unravel" - Bernie Madoff, maybe https://t.co/CZJRLTtAbk
— zerohedge (@zerohedge) February 27, 2026
Let's revisit our notes on the "circle jerk" AI vendor financing schemes as we've pointed out since last fall (read here & here).
Related:
The circle jerk keeps getting larger.
Tyler Durden Fri, 02/27/2026 - 09:10"Persons may wish to consider leaving Israel while commercial flights are available," the US State Department announced Friday, signaling that US strikes on Iran could be imminent,.
It provided confirmation the US government has begun evacuating "non-emergency" personnel from the embassy in Israel and their family members, citing "safety risks" amid growing tensions with Iran.
 via AFP
via AFP
The new urgent announcement also strongly suggests that whatever military action ensues, it will mostly likely involve a joint operation between the US and Israel. Some have warned that Washington is essentially about to go to war on behalf of what are fundamentally Israel's interests in the region.
People in Israel would further be at risk given the potential for Hezbollah to renew strikes on the country's north, and then there's the threat of Houthi attacks from the south - as happened in the last conflict in June and prior.
Fox correspondent Lucas Tomlinson has noted that the last time the embassy issued such an evacuation notice it occurred just eight days before Operation Midnight Hammer (the June strikes).
Another regional journalist, Idrees Ali, as observed: "Many of the things that happened before the United States and Israel struck Iran last year are happening now."
But this time around the military build-up by the United States is much, much bigger - and days ago hit levels not seen since the 2003 Bush-ordered invasion of Iraq.
On February 27, 2026, the Department of State authorized the departure of non-emergency U.S. government personnel and family members of U.S. government personnel from Mission Israel due to safety risks.
— U.S. Embassy Jerusalem (@usembassyjlm) February 27, 2026
In response to security incidents and without advance notice, the U.S.… pic.twitter.com/aWzX6Gk36x
Axios also confirms that while the US Embassy is still operating for now, "US ambassador Mike Huckabee wrote in a message to embassy staff that whoever wants to leave the country should do so Friday."
The State Dept. notice states further, "The ambassador, diplomats and U.S. personnel working on assistance to U.S. citizens, security, military, political and intelligence affairs will stay in the country."
Canada has also newly issued a warning Friday for its citizens to leave Iran and the Mideast region, warning about the near future availability of commercial travel.
Starting the countdown to yet another major US initiated war in the Middle East?...
Everything appears to be in place. Additional F-35s have been deployed, refueling tankers have reached their designated positions with more en route, and the USS Gerald R. Ford has arrived in Israeli waters. And no deal on the nuclear issue still. https://t.co/YP9t8oQ3AL
— Levent Kemal (@leventkemaI) February 27, 2026
This adds to a growing list of countries telling their population to avoid the region or leave, including: Finland, Serbia, Poland, Sweden, India, Greek Cyprus, Singapore, Germany, Brazil, and others. China has also told its citizens in Israel to be prepared for an emergency and to prepare to leave the country. Any Chinese traveling in Iran are also being told to depart immediately.
Tyler Durden Fri, 02/27/2026 - 08:50US Producer Prices came in hotter than expected in January, with the headline PPI rising 0.5% MoM (vs +0.3% exp), higher than the revised +0.4% MoM in December. This left Producer Prices up 2.9% YoY (hotter than expected but below December's +3.0%)...
Source: Bloomberg
Under the hood, we see a surge in Services costs (not tariff related) dominated the rise in PPI (while Energy saw deflation)
Final demand services: The index for final demand services advanced 0.8% in January, the largest increase since moving up 0.9% in July 2025. Most of the January rise in prices for final demand services can be traced to margins for final demand trade services, which jumped 2.5 percent. (Trade indexes measure changes in margins received by wholesalers and retailers.) Prices for final demand transportation and warehousing services advanced 1.0 percent, while the index for final demand services less trade, transportation, and warehousing was unchanged.
Final demand goods: Prices for final demand goods moved down 0.3% in January, the largest decrease since falling 0.7% in March 2025. Leading the January decline, the index for final demand energy dropped 2.7 percent. Prices for final demand foods decreased 1.5 percent. In contrast, the index for final demand goods less foods and energy advanced 0.7 percent.
The Energy component of PPI could be about to re-accelerate...
Core PPI (ex food and energy) surged 0.8% MoM and is up 3.6% YoY (both hotter than expected) - the fast pace of price increase since March 2025...
Source: Bloomberg
Margin pressures remain as input prices rise faster than output prices...
The bottom line is that this will likely lead to a hotter than expected Core PCE print - something The Fed watches closely.
Tyler Durden Fri, 02/27/2026 - 08:42The rollercoaster continues: US equity futures are in the red again, trading near session lows, and set to extend Thursday's losses with as stocks underperform after yesterday's spectacular plunge in the momentum trade as NVDA's post record-breaking earnings/guidance plunge spooked markets that nothing is resolved about where AI goes next. As of 8:00am ET, S&P futures were down 0.6%, and set for a monthly loss after a whirlwind February marked by twin fears of a bubble in the AI trade and of the technology’s disruptive power. Nasdaq futures dropped 0.7%. In the latest AI contradiction, CoreWeave plunged 12% after data center operator reported a bigger-than-expected loss and higher capex fueling concern about overspending on infrastructure. But in a mirror image, Dell is 12% higher after its outlook for sales of AI servers exceeded estimates, a sign of robust demand for machines helping fuel the AI data center build-out. 10-year Treasury yields slid below 4%, while the USD is flat. Commodities are mixed, with Energy higher and Metals mixed (Silver outperforming vs Gold flat). Today's macro data focus is on PPI and Construction Spending.
In premarket trading Mag 7 stocks are mixed: Nvidia is up 0.4% after sliding Thursday, other names are mostly lower (Alphabet little changed, Tesla -0.2%, Amazon -0.5%, Apple -0.5%, Meta Platforms -0.5%, Microsoft -0.8%).
In other corporate news, Netflix rose more than 7% after dropping out of the bidding for Warner Bros. Dell Technologies surged 11% following a strong sales forecast for its AI servers.
Nvidia suffered its worst day since April on Thursday, with the price action suggesting the world’s most valuable company is no longer being rewarded for spectacular results and remarkable guidance.
NVDA's plunge happens as the disruptive potential of AI has rattled US equities for weeks in what traders have dubbed the “AI scare trade.” The technology’s bellwethers have also lost momentum after powering S&P 500 gains for years, prompting investors to rotate into markets abroad and companies tied to broader economic growth.
“The outperformance highlights the possibility of a lingering overvaluation in some asset classes in the US, as well as doubts about the independence of the Federal Reserve’s future monetary policy,” said Guillermo Hernandez Sampere, head of trading at asset manager MPPM. “Barring an economic downturn in Europe, the outperformance should continue.”
“The outperformance highlights the possibility of a lingering overvaluation in some asset classes in the US, as well as doubts about the independence of the Federal Reserve’s future monetary policy,” said Guillermo Hernandez Sampere, head of trading at asset manager MPPM. “Barring an economic downturn in Europe, the outperformance should continue.”
As Wall Street tries to assess likely job losses at the hands of AI, Jack Dorsey’s financial technology firm Block is cutting 4,000 employees, nearly half its workforce, in a bet on AI changing the future of labor productivity. Then again, considering that Elon Musk fired 80% of Dorsey's last company before ChatGPT was even out - and it thrived - or that Block spent $68 million on a party a few months before the mass layoffs, suggests that the culprit here is bloat and terrible management, and not AI.
Block:
— zerohedge (@zerohedge) February 27, 2026
1. spend $68 million on a party
2. 200 days later fire 40% of workers
3. blame AI pic.twitter.com/TdgXnIVGNM
The market’s unease about private credit persists. In an rerun of the collapse of First Brands, a spectacular new private credit blowup in London has Wall Street chasing billions. And a private credit fund overseen by Apollo Global Management cut its dividend and marked down the value of its assets amid signs of strain in parts of its loan book.
Elsewhere, Anthropic, the AI start-up that has wiped billions off the market value of US stocks, remains in focus. US lawmakers, flummoxed by the Pentagon’s negotiating tactics, are warning that carrying out those threats would have significant consequences for the military ecosystem. Meanwhile, investment-grade bond markets, which had emerged as a safe haven during recent AI-driven swings in equities, are starting to show signs of strain.
US stocks saw inflows of $2.2 billion in the week ended Feb. 25, according to BofA citing EPFR Global data. Strategists led by Michael Hartnett see international stocks outperforming US for the rest of this decade.
"I don’t see any major correction coming, but any hint of a recession linked to AI in the US would certainly trigger some unpleasant trading,” said Andrea Tueni, head of sales trading at Saxo Banque France. “Europe is currently better positioned than the US and outperforming as its tech sector is much smaller and there is much less uncertainty on monetary policy.”
Earnings season wraps up next week, and has so far been somewhat disappointing, with the fewest S&P 500 companies beating estimates since 2022. Of the 481 to have reported so far, 73.4% have beaten forecasts, while nearly 22% have missed. No major US companies are expected to report on Friday, but Berkshire Hathaway’s annual report is due on Saturday, including Greg Abel’s first annual letter to shareholders on performance since taking over as CEO from Warren Buffett.
Europe’s Stoxx 600 was on track for an eighth straight monthly advance, its longest such streak in more than a decade; telecommunications and mining stocks lead gains, while travel and consumer products shares edged lower. Here are the biggest movers Friday:
Asian stocks traded mixed, with a key regional benchmark on track to close its best February on record as investors snapped up shares of the region’s AI infrastructure companies. The MSCI Asia Pacific Index gain as much as 0.6% Friday. South Korea’s Kospi fell 1%, as chipmakers Samsung and SK Hynix fell. Key gauges rose in Japan and Hong Kong, while Taiwan’s market was closed for a holiday. Asian stocks have been outperforming global peers, with the region’s hardware firms seen as beneficiaries of the AI buildout even as concerns grow over spending levels and business disruption. The MSCI regional gauge is up 6.7% this month, poised for the best February since it started trading in 1998. Chinese technology stocks in Hong Kong capped their worst month in two years, weighed by weak earnings and a lack of buying by mainland investors. Sentiment toward China’s Internet giants has cooled amid concerns over valuations and rising competition that’s eroding corporate bottom line. Meanwhile, global investors offloaded nearly $5 billion of South Korean equities on Friday, in a sign of profit taking after the equity benchmark rallied nearly 50% this year. The index rose past the 6,000 threshold this week, just a month after surpassing President Lee Jae Myung’s political goal of 5,000.
In FX, the dollar was set for a fourth straight monthly loss. The Norwegian Krone led G10 currencies with a +0.54% rise. The pound fell slightly against the dollar after a special election in the UK laid bare the unpopularity of Prime Minister Keir Starmer’s government.
In rates, treasuries extended gains, with the 10-year note on track for its best month in a year after yields have tumbled 26 basis points in February to 3.98%. Outperformance by front-end and belly steepened 2s10s spread by about 1bp, 5s30s by about 1.5bp. 10-year gilts and bunds are slightly cheaper vs US benchmark
In commodities, oil rose again, after sliding on Thursday. Gold traded flat, with prices headed for a seventh consecutive monthly advance.
The cross-asset moves reflect sustained demand for havens amid policy uncertainty from the Trump administration, tensions in the Middle East and questions about the strength of US economic growth. Swap traders added to bets on Federal Reserve interest-rate cuts, with a July move again almost fully priced after being briefly scaled back earlier this week.
US economic data slate includes January PPI (8:30am), February MNI Chicago PMI (9:45am, several minutes earlier for subscribers), December construction spending (10am) and February Kansas City Fed services activity (11am). No Fed speakers are scheduled. Bloomberg Economics expects producer price inflation, which shows price trends before they reach consumers and feeds into the Fed’s preferred gauge of inflation, the personal consumption expenditures index, to have slowed to 0.2% in January from 0.5%. Potentially, that could bolster the case for further rate cuts.
Market Snapshot
Top Overnight News
Trade/Tariffs
A more detailed look at global markets courtesy of Newsquawk
APAC stocks were ultimately higher heading into month-end but with price action choppy following the weak handover from the US, where sentiment was clouded by tech weakness, while participants also digested the recent US-Iran talks in Geneva. ASX 200 mildly gained as strength in tech and telecoms atoned for the losses in financials and consumer stocks. Nikkei 225 traded indecisively amid a firmer currency and a slew of mixed data releases from Japan, in which Industrial Production disappointed, Retail Sales topped forecasts, and Tokyo CPI printed firmer-than-expected but slowed across the board with the Core reading falling beneath the central bank's 2% price target for the first time since October 2024. Hang Seng and Shanghai Comp were varied with outperformance in Hong Kong as participants digested earnings releases from the likes of Baidu and Sun Hung Kai Properties, while the mainland initially lacked direction in the absence of fresh catalysts and ahead of next week's annual "two sessions", while Trump-Xi summit preparations were said to falter. However, late upside was seen after comments from China's Politburo meeting in which it stated that China's development process during the 14th Five-Year Plan is extraordinary and that it is necessary to continue to implement a more active fiscal policy and a moderately loose monetary policy.Top Asian News
Top Asian News
European bourses (STOXX 600 +0.3%) are broadly firmer, with the SMI (+0.7%) the clear outperformer after Swiss Re (+3.6%) posted a 47% Y/Y rise in 2025 net profit while announcing a USD 500mln share buyback. Lagging behind its peers is the CAC 40 (-0.1%), with very company-specific news to drive the index. European sectors are mixed. Telecommunications (+1.3%) outperform after Spain's Cellnex (+0.6%) saw 2025 operating profit rise more than double annually and Telefonica (+3.7%) reportedly negotiating the purchase of 1&1 (+9.4%)in Germany in a EUR 5bln deal. On the flip side, Travel and Leisure (-1.8%) is underperforming despite positive IAG (-5.5%) earnings, in which the Co. beat FY profit expectations and announced a EUR 1.5bln share buyback.
Top European News
FX
Fixed Income
Commodities
Geopolitics: Middle East
Geopolitics: Others
US Event Calendar
DB's Jim Reid concludes the overnight wrap
d
Tyler Durden Fri, 02/27/2026 - 08:30UK Prime Minister Keir Starmer is under pressure to reinvent his ailing Labour government with a leftwards pivot after the Green Party captured one of its House of Commons seats via a special election.
The result underscores the recent fragmentation of UK politics and the disruption of long-held electoral certainties.
It has “torn the roof off” British politics, said Green Party Leader Zack Polanski.
Spencer’s win marks the first-ever by-election victory for the Greens, as well as their first seat in northern England, highlighting the increasing reach of the left-wing party in a context where Labour voters are abandoning it in both directions.
Spencer’s margin of victory was much more comfortable than commentators had expected, with polls consistently understating the Greens’ appeal.
The swing from Labour was 26% in Gorton and Denton, and the Greens now have five MPs in Parliament.
Andrea Egan, general secretary at workers’ union Unison, said Labour should be “taking the fight” to Reform UK Leader Nigel Farage “rather than letting him set the agenda.”
As Tom Jones reports below for TheCritic.co.uk, the election has grim implications.
The Gorton and Denton by-election, by virtue of having been won by the Greens, marks a more momentous shift for the left than the right. Ava Santina has written about this for us, and a recent Critic Show episode is devoted entirely to the fracturing of the left.
But like the overweight kid trying to avoid getting near the ball in PE, just because you don’t win, that doesn’t mean there aren’t lessons to be learned.
The first is that Reform may need to start thinking about expectation management. As an insurgent party, they were happy to talk up their chances of winning in order to build the narrative that the two main parties are finished. But this made the race seem closer than the result ended up being: 4,000 votes behind the Greens and just over 1,000 votes ahead of Labour therefore will be made to seem like an underperformance by the media.
It was not. In terms of the size of the swing needed from the 2024 General Election, Gorton and Denton was 413th on Reform’s target list. Even with their polling shoring up at around 30 per cent, as it is in national polls, turning the sixth Labour seat over was a stretch too far. On the upside, a national campaign against the Greens will be a much more favourable proposition for Reform, coming as it does against a weaker campaigning machine than Labour — and increased scrutiny on the Green Party, which it will fail.
A lesson may also be on the need to find local candidates. I hate that local candidates boost election performances, I hate that Hannah Spencer claimed she had never seen Matt Goodwin in the local Asda “doing his big shop”, but most of all I hate that it works. A local candidate would not have swung Gorton and Denton their way, but there will be a significant number of seats where it will. It’s yet another problem for Reform’s candidate selection team to deal with.
As for the other right-wing parties, the question is, “why bother?”
The Conservatives took just 706 votes. 1.9 per cent of the vote. That is their lowest ever vote share in a by-election. They lose their deposit for the first time at an English by election for nearly 40 years.
We have heard much about the need for a Reform-Conservative pact. It has come, overwhelmingly, from establishment media figures whose professional relevance depends on preserving their access to the Conservative Party — and who can see that access, and therefore their own influence, draining away. Such a pact would necessitate the Conservatives to stand aside in hundreds of seats like this. It is so ingrained in the Conservative psyche to stand candidates everywhere that it is part of the party’s constitution. Farage has been burned before with a Conservative pact — it is incumbent on the Conservatives to make any such a deal happen.
The Conservative statement after the result spoke much about this result rendering Starmer a lame duck, but nothing about their failure to play any role in this result being delivered.
Meanwhile Advance UK, the Ben Habib vehicle, took 154 votes — less than the Monster Raving Loony Party. A vision of Restore Britain’s future? Perhaps. There is a question here. If things are really as bad as the leaders of these parties claim, then how can they justify siphoning off votes from adjacent right-wing parties over ever-finer points of right-wing doctrine? When the house is on fire, it is a strange moment to insist on arguing about the exact brand of extinguisher.
Perhaps parties formed with the sole aim of giving histrionic social media addicts something to do will not be Britain’s salvation. Who knew.
Finally, the lesson that all parties of the right should take is in the dangers of sectarian voting.
For a long time the conventional parties have been happy with sectarian voting, so long as it delivered conventional parties.
The salience of the Muslim vote in this election — coupled with the Green Party’s campaign videos in Urdu and Bangla — has reinforced a narrative that has been gathering force since the rise of the so-called “Gaza independents”: that Britain has a sectarian voting problem that can no longer be ignored.
It is fast becoming an ingrained part of our political culture: Sky’s coverage of the result included Sam Coates examining and speaking about the proportion of the seat that is ethnic minority.
There is a risk here.
A political class steeped in American news and habits of thought may interpret this development as merely the British version of familiar US-style demographic politics, where politics is more attuned to minute changes amongst identity and interest groups.
It is not. American immigrants, and therefore their voting patterns, are markedly different to those in Britain. We are not getting “suburban moms”.
The Electoral Commission grants Democracy Volunteers access to polling stations during elections, and the group has reported seeing “concerningly high levels” of family voting (an illegal practice in which two voters occupy a single polling booth, often with one directing the other’s vote) in the by-election.
John Ault, director of Democracy Volunteers, said: “Today we have seen concerningly high levels of family voting in Gorton and Denton. Based on our assessment of today’s observations, we have seen the highest levels of family voting at any election in our 10 year history of observing elections in the UK.”
He added: “We rarely issue a report on the night of an election, but the data we have collected today on family voting, when compared to other recent by-elections, is extremely high. In the other recent Westminster parliamentary by-election in Runcorn and Helsby we saw family voting in 12 per cent of polling stations, affecting 1 per cent of voters. In Gorton and Denton, we observed family voting in 68 per cent of polling stations, affecting 12 per cent of those voters observed.”
Manchester City Council have hit back, arguing that “No such issues have been reported today”, and blaming Democracy Volunteers for not reporting these issues at the time. This issue is too obvious to ignore (although some will try), and at least some parties will find it politically expedient to oppose it. These voting patterns have been documented for a long time. Perhaps, after the next election, we will finally have the chance to deal with them. Small mercies, but mercies nonetheless.
Angela Rayner, the former deputy prime minister who is bookmakers’ favorite to succeed Starmer, said the result was “a wake-up call.”
Tyler Durden Fri, 02/27/2026 - 08:25It's a disturbing commentary on our times when the concept of men and women being required by law to admit their proper biological sex becomes headline news, but here we are.
For the past decade, transgender ideology (with zero basis in scientific reality) has surged to the forefront of our cultural zeitgeist. Never before in the history of the western world has one tiny minority of people received so much privilege and protection from governments and the corporate establishment. Furthermore, this small group of mentally ill people has triggered a political firestorm that is changing the face of the US.
Why did the Democratic Party and so many wealthy and powerful elites choose transgenderism as the hill to die on? Why do they lie and claim there are no differences between men and women? Why do they want to give unhinged men access to women's bathrooms and locker rooms? Why are they so intent on indoctrinating children with gender fluid propaganda? Why do they want to let little kids mutilate their bodies with sex hormones and surgeries? It's hard to say.
One's first inclination is to assume that these people are evil. How else can we explain their behavior? The other consideration is that they are all suffering from mental instability. At bottom, there is no place for transgender ideology in a civilized society, and it would appear that the Kansas GOP has come to the same conclusion.
Kansas has recently enacted a law that restricts transgender individuals from using bathrooms, locker rooms, and similar multi-occupancy facilities in government-owned or leased public buildings (such as schools, universities, and state facilities) that do not align with their sex assigned at birth. The legislation, known as House Substitute for Senate Bill 244 (SB 244), requires people to use single-sex facilities based on their biological sex at birth.
The new law also requires trans activists to use their real biological sex assigned at birth on their driver's licenses, birth certificates and other official documents. In other words, the LARP is over, at least in Kansas.
Violators could face civil lawsuits, with a minimum of $1,000 in damages for each instance where someone believes they shared a facility with a transgender person (often described as a "bounty-style" provision). Repeated violations can lead to criminal penalties
Democratic Gov. Laura Kelly vetoed the measure but the Legislature’s GOP supermajority overrode it last week. Republican state lawmakers across the U.S. have pursued a series of measures to prevent a repeat of the Biden era, which resulted in a dizzying avalanche of trans related special protections and privileges, essentially making transgender activists into an elite class of citizen.
Western allies like Canada, Australia and parts of Europe have gone even further, making it a criminal offense to criticize trans concepts or trans activists online. The US is the only country so far to reverse course.
Not surprisingly, the number of people affected by the law is minimal. Only 1700-1800 individuals will end up having to change the drivers license or birth certificate. Consider for a moment, though, that an entire state was being held hostage by only 1800 people. Why would any society adapt so many standards and practices for a such meaningless percentage of the population?
Tyler Durden Fri, 02/27/2026 - 07:45Authored by Laura Hollis via The Epoch Times,
There’s a revolution brewing across the Big Pond.
The British people were already fed up with the Labour government headed by Prime Minister Keir Starmer. And then the man Starmer appointed to be ambassador to the United States—Peter Mandelson—was exposed as having a deep friendship with sex predator Jeffrey Epstein, even after Epstein was convicted on charges of sex with a minor in 2008. Mandelson is now under investigation for possibly passing sensitive government information to Epstein. Starmer is viewed as being crippled by these revelations and losing support within his own party.
But it’s the split on the political Right that is most interesting at the moment. For quite some time, Nigel Farage’s Reform UK Party has been the favorite to unseat Labour in the next general parliamentary election in 2029. Farage came into the international spotlight as the leader of the movement to take Britain out of the European Union (“Brexit”). But Farage is increasingly viewed as having become “establishment,” particularly on the question of what to do about the millions of Muslim migrants who have poured into England and the rest of the United Kingdom.
Farage and former fellow Reform UK MP Rupert Lowe had a serious falling-out last year.
Lowe was—and is—pushing for mass deportations, a policy that Farage has dismissed as “beyond the point of reasonableness, of decency, of morality.”
Lowe publicly criticized Farage’s leadership of Reform UK; Farage responded by kicking Lowe out of the party, accusing him of “bullying” staff members and of making threats against party chairman Zia Yusef. It would further appear that Farage was responsible for a police raid on Lowe’s home to confiscate his firearms. (No charges were filed against Lowe, and his guns were returned to him.)
Lowe has returned with a vengeance. Two weeks ago, he announced the formation of a new political party, “Restore Britain.”
“Restore,” as it is now commonly referred to, makes nearly daily policy pronouncements on social media platform X.
Among the policies Lowe says the party will advocate for are banning the burqa, return of the death penalty for the most heinous crimes, stronger self-defense protections for British homeowners, reversal of convictions for those accused of “hate speech crimes” and commutation of their sentences, laws ensuring freedom of speech, and mass deportations, starting with migrants who have committed crimes, including and especially the men who have participated in the “rape gangs.”
Perhaps more than any other issue, this one has galvanized the British public. People are shocked to discover that the government was too timid to arrest and prosecute men—largely Pakistani—who were known to be keeping young girls as sex slaves, fearing being called racist. Lowe has sworn he’ll bring all the facts to light and earlier this week released a victim’s statement indicating that members of local police forces were not only aware of the Pakistani rape gangs but, in some cases, were participants.
All of this has created a perfect storm of outrage, and Lowe has very clearly hit a nerve.
Restore Britain has acquired 100,000 members in less than two weeks. To put things in perspective, that places Restore Britain fifth—behind the top four political parties—by membership: Reform UK currently has 280,000 members, Labour 250,000, the Green Party 198,000 and the Conservative Party 123,000.
In his inimitable fashion, X CEO Elon Musk has weighed in, expressing support for Restore Britain.
Their X account now has over 300,000 followers, and videos posted are generating millions of views. Even Americans—who cannot vote or become members of any British political party—are throwing in financial support for Lowe’s Restore party. X is filled with fan art, posters, memes and slogans backing Restore Britain and Lowe. (A favorite is “Aim High—Vote Lowe.”)
The British parliamentary system is very different from America’s political structure, and their general election is—absent some intervening event—three years away. But this feels for all the world like a MAGA-esque revolution in the making. On the Left, the dominant party is Labour—presently in power—which defends unlimited migration into the UK, insists that Muslims add to the rich tapestry of British culture, refuses to conduct an inquiry into the Pakistani rape gang investigations, and prosecutes citizens who complain about the impact of mass migration: the crime, the outrageous government expenditures, the benefits given freely to migrants (while native British struggle to find housing and wait for health care), the unprosecuted rape of thousands of white British girls, and the denigration of British society and culture.
On the Right, the Tories have traditionally dominated. But that party saw five weak prime ministers within 14 years (Rishi Sunak, Liz Truss, Boris Johnson, Theresa May, David Cameron), leaving it without much public support, and creating the possibility that Reform UK will have the greatest number of seats in the next parliament, and party leader Nigel Farage will become prime minister.
At least, that was the narrative until a couple of weeks ago. Now Restore Britain is being viewed by its supporters—much as Donald Trump was in 2015—as the dark horse that might surprise everyone in 2029.
Polls conducted this week asking Britons their voting intentions show Restore Britain—which is not even an officially approved party yet—already with 7 percent support. (Keep in mind that these numbers are divided among 10 political parties, with Reform UK having the largest percentage, at 25 percent.) Reform UK is trying to stave off defections, insisting that Restore Britain will “split the vote,” and cannot possibly get enough seats in Parliament to elect the prime minister, thus handing victory to Labour again (or, God forbid, the Green Party).
But this is exactly what establishment Republicans in the United States said when Trump entered the presidential race in 2015.
In the UK now, as in the U.S. then, citizens are disgusted with traditional political parties and their government’s inability—or refusal—to perform what is viewed as its most fundamental responsibility—protecting the British public and preserving the country.
It’s going to be fun to watch.
Tyler Durden Fri, 02/27/2026 - 07:20Readers have been briefed on the emerging global high-bandwidth memory (HBM) supply crunch, driven by soaring data center demand. We have tracked the progression of this theme for months through what seem to be almost weekly developments, ranging from notable institutional research desks and industry insiders to more recent warnings from electronics device companies about looming shortages and price spikes.
Now, market research firm International Data Corporation (IDC), which tracks handset shipments, has issued an apocalyptic warning: the smartphone market is headed for a historic downturn due to a memory crunch.
IDC estimates that global smartphone shipments will plunge 12.9% in 2026 to 1.1 billion units, the lowest annual level in over a decade. This outlook is much gloomier than IDC's November forecast.
“What we are witnessing is not a temporary squeeze, but a tsunami-like shock originating in the memory supply chain, with ripple effects spreading across the entire consumer electronics industry,” wrote IDC Vice President for Worldwide Client Devices, Francisco Jeronimo.
Jeronimo continued, “The global smartphone market, particularly Android manufacturers, faces a significant threat. Vendors whose business is mainly at the low end of the market are likely to suffer the most."
"Rising component costs will hit their margins, and they will have no choice but to pass the costs on to end users. By contrast, Apple and Samsung are better positioned to navigate this crisis. As smaller and low-end-positioned Android vendors struggle with rising costs, Apple and Samsung could not only weather the storm but potentially expand market share as the competitive landscape tightens," he explained.
IDC Senior Research Director Nabila Popal, who was quoted by Bloomberg, said, "The tariffs and pandemic crisis seem a joke compared to this."
Popal warned, “The smartphone market will witness a seismic shift by the time this crisis is over — in size, average selling prices and competitive landscape. We don’t expect the situation to ease up until mid-2027, at least.”
Counterpoint, another research firm that tracks handset shipments, published a similarly dire forecast earlier today, warning of a 12.4% decline in global smartphone sales this year. The note also warned of a “full-scale supply shock” related to the HBM supply crunch.
“2026 is shaping up to be the worst year in smartphone history,” Counterpoint analyst Yang Wang said. “The industry has never seen a drop this steep.”
As the memory crunch storm approached, we told readers to prepare:
Goldman's Meeting With Top Memory Supplier Points To Higher Prices As Crunch Worsens
That Escalated Quickly: Goldman Cuts PC Shipment Outlook As Memory Prices Go Parabolic
Professional subscribers have been provided with notes on the memory crunch storm and can read them on our new Marketdesk.ai portal.
Tyler Durden Fri, 02/27/2026 - 06:55My end-of-week morning train WFH reads:
• People Loved the Dot-Com Boom. The A.I. Boom, Not So Much.: The dot-com era generated genuine public excitement. The AI boom is generating anxiety, skepticism, and resentment — even as the money keeps pouring in. (New York Times)
• Constellation Brands: The Fastest Growing Beer Company in America: The parent company of Modelo and Corona has been on a tear, riding the wave of shifting American beer preferences and demographic change. (Fiscal.ai)
• Luxury’s Overexposure Is Biting: The luxury sector bet on ubiquity — logos everywhere, collabs with everyone, accessibility as strategy. Now the bill is coming due as exclusivity evaporates. (Matter / Substack)
• Crypto Is Pointless. Not Even the White House Can Fix That.: Despite unprecedented government support, crypto still hasn’t found a reason to exist beyond speculation. The problem was never regulation — it was utility. (New York Times)
• The Biggest New Fans of 401(k)s Are Small Businesses: New tax incentives and simpler plan structures are driving a wave of small businesses offering retirement plans for the first time. (Wall Street Journal)
• The Trump ‘Affordability’ Pivot That Never Came: The president promised to bring down costs for working families. Heading into the State of the Union, housing, groceries, and healthcare are all still crushing household budgets. (The Bulwark)
• 10 Least Reliable Cars of 2026: Consumer Reports’ annual survey of 380,000+ vehicles names the models most likely to leave you stranded. (Consumer Reports)
• Across the US, people are dismantling and destroying Flock surveillance cameras: Citizens are taking matters into their own hands, physically removing the license plate reader cameras that have quietly blanketed American cities. (Blood in the Machine)
• How scammers are using AI deepfakes to steal money from taxpayers: AI-generated voices and faces are being used to impersonate government officials and steal public funds. The fraud is getting more sophisticated faster than defenses can keep up. (Washington Post)
• How Did Hendrix Turn His Guitar Into a Wave Synthesizer?: Jimi Hendrix was a systems engineer who happened to play guitar. A technical breakdown of how he precisely controlled modulation and feedback loops to create sounds nobody had heard before. (IEEE Spectrum)
Be sure to check out our Masters in Business next week with Jeff Chang, cofounder and President of VEST. The firm manages over $55 billion in client assets across various “Buffered” and “Target Outcome” strategies. Backed by Y Combinator, the firm launched in 2012 and pioneered an approach to portfolio construction based on defined outcomes and engineered certainty.
Irrational Exuberance vs Chat GPT Launch (No earnings versus earnings)
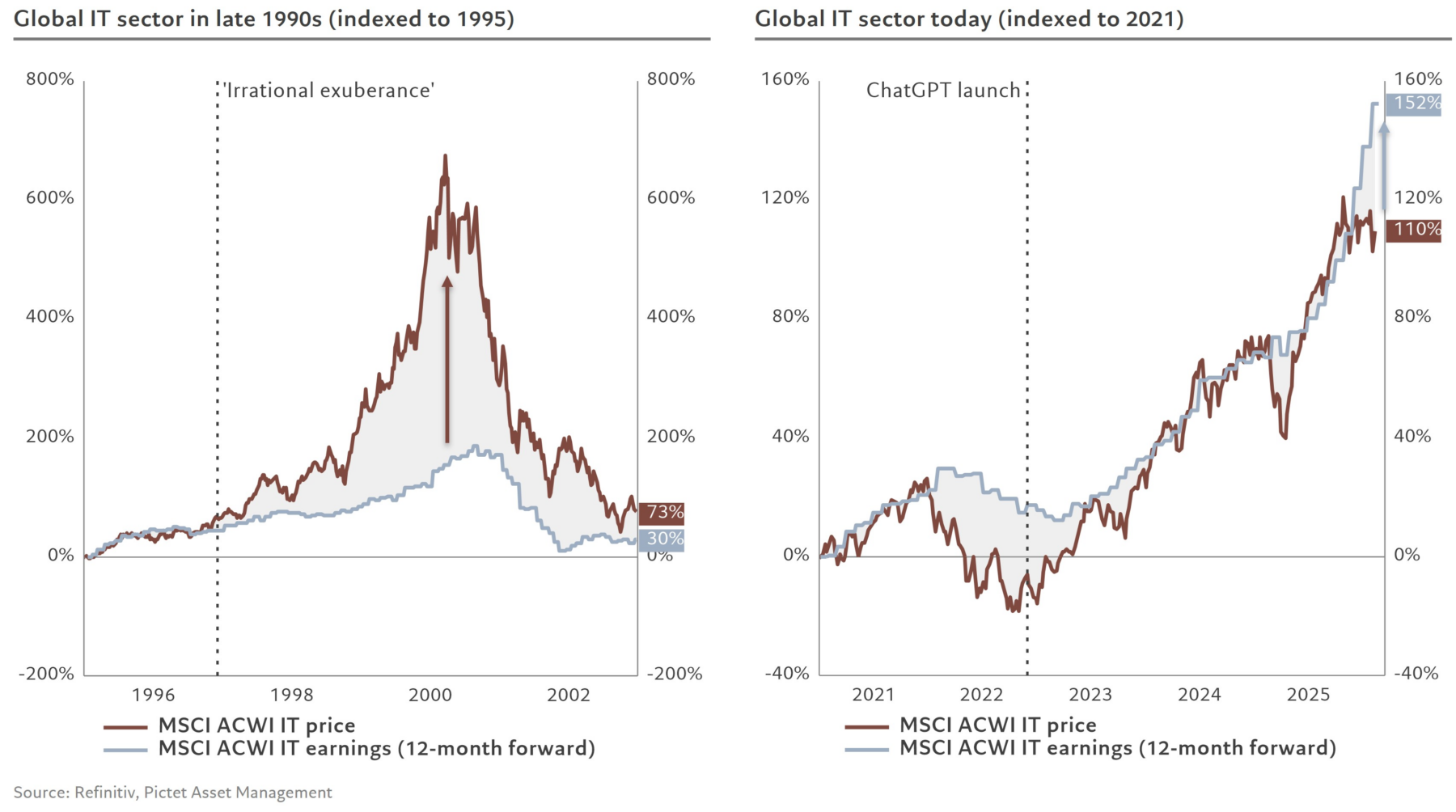
Source: @steve_donze
Sign up for our reads-only mailing list here.
The post 10 Friday AM Reads appeared first on The Big Picture.
Authored by Paul Bradford via American Greatness,
For years, some of the worst actors in the tech industry were able to do as they pleased without fear of consequence.
They could construct monopolies, censor conservatives, and promote wokeness as much as they wanted. But things are beginning to change with the Trump administration. Thanks to the efforts of the White House, the days of Big Tech wantonness are over. These companies now must follow the basic tenets of the free market and stop suppressing views they disagree with.
One of the leaders in this effort to correct Big Tech is FTC Chairman Andrew Ferguson.
His agency recently announced it would ramp up its scrutiny of Microsoft and its allegedly anti-competitive practices. The FTC accuses Microsoft of advancing monopolistic practices in making it very difficult for customers to use the company’s signature products—such as Windows and Office—on rival cloud services. The agency is requesting information from both the tech giant and the companies affected by these malicious policies.
Microsoft is one of the worst offenders in the category of Big Tech malpractice. From dubious business practices to close ties to the Chinese Communist Party, Bill Gates’s company sets the bar for how low these giants can go. The China connection is particularly disturbing, as American Greatness has previously covered. Microsoft has allegedly shared information from Windows and Office code with elements tied to Chinese intelligence, allowed its cloud infrastructure to be compromised by Chinese assets, and had several of its initiatives work closely with partners from the Chinese defense industry. Microsoft certainly doesn’t put America first.
It also doesn’t respect conservative opinions. The tech giant touts one of the most aggressive records of censorship against the Right. Microsoft was one of the major backers of NewsGuard, a service that promoted itself as a guide to media reliability. Instead, it acted as a liberal hall monitor that suppressed conservative news sources and insisted on liberal framing of events. Thanks to NewsGuard, it became harder for internet users to find alternative viewpoints to the partisan mainstream media.
Microsoft is deserving of greater scrutiny due to its practices.
But Ferguson isn’t just focused on this one egregious offender. He’s dedicated to taking on all bad actors in the industry.
The FTC recently sent a letter to Apple, warning the tech giant to stop suppressing right-leaning sources and elevating leftist ones.
Ferguson wrote in the letter:
Big Tech companies that suppress or promote news articles in their news aggregators or feeds based on the perceived ideological or political viewpoint of the article or publication may violate the FTC Act if that suppression or promotion (1) is inconsistent with the terms and conditions of service; (2) is contrary to consumers’ reasonable expectations such that failure to disclose the ideological favoritism is a material omission; or (3) when those practices cause substantial injury that is neither reasonably avoidable nor outweighed by countervailing benefits to consumers or competition.
One of his first moves as Trump’s FTC chairman was to announce an investigation into Big Tech censorship.
The agency declared in its announcement of the inquiry, “Censorship by technology platforms is not just un-American, it is potentially illegal.”
The investigation encouraged Americans who have suffered from tech censorship and deplatforming to share their stories with the agency.
Last year, Ferguson reached an agreement with Omnicom, the biggest ad agency, to end discrimination against online ads for political reasons.
Many right-leaning companies and candidates have been affected by such discrimination.
Ferguson ensured that one of the main bodies responsible for it would no longer do so.
Ferguson’s actions are a refreshing and stark contrast to those of Trump’s first-term FTC Chairman Joe Simons, who defied a modest Trump executive order to go after Big Tech companies that deceived consumers about their censorship practices.
With officials like Andrew Ferguson, the second Trump administration is doing its utmost to solve these issues. Continuing the antitrust investigation of Microsoft is an important component of this strategy.
Tyler Durden Fri, 02/27/2026 - 06:30Cocoa prices have collapsed 75% from their 2024 peaks, and Goldman’s latest note points out that the worst of the cocoa shock for chocolate makers may finally be passing after being squeezed by soaring bean costs through 2023, 2024, and into the first half of 2025. This only suggests that lower chocolate bar prices at the supermarket could materialize later this year. Against that backdrop, Goldman reiterated Buy ratings on two confectionery stocks.
Analysts led by Sam Darbyshire said the global chocolate production costs should drop by as much as 10% in 2026 and 2027. She pointed out that weather patterns in West Africa - the mecca of global cocoa farming - have supported increased production for the upcoming harvest, leading to stabilization in global supplies.
Darbyshire pointed out that the cocoa futures curve is no longer backward-dated, with December 2027 delivery now 17% more expensive than March 2026 delivery. She said this would help top confectionery firms to commit to increased volumes.
"Double-digit raw material deflation in chocolate over the next two years is likely to drive an increasingly competitive operating environment as manufacturers strive to return to volume growth," she wrote in the report.
Darbyshire noted that, with elevated chocolate prices, current Nielsen data show that consumer demand for chocolate remained soft in January, with elasticities worsening in Europe (consistent with Mondelez commentary). She said that private players are being more competitive on pricing, with Mars and Ferrero pricing below market.
"With weak underlying volumes and easing raw material inflation, we expect promotional activity to intensify throughout the year," the analyst said.
Darbyshire said this new cocoa pricing regime has generated a "Buy" in Barry Callebaut and Nestle, but "Sell" in Lindt.
Why this matters is that the chocolate industry is about to transition from a period of price hikes to one of greater discounting and tougher competition.
In a separate note, Bonnie Herzog, managing director and senior consumer analyst at Goldman, highlighted in December that sliding cocoa prices could produce "tailwinds" for candy and junk food companies. Read that note here.
Professional subscribers can read the full note on the inflection point the chocolate industry is entering this year, along with many more charts via Goldman, on our new MarketDesk.ai portal. As noted above, attractive setups are emerging in several beaten-down candy stocks.
Tyler Durden Fri, 02/27/2026 - 05:45China has removed nine military lawmakers from its national parliament, escalating President Xi Jinping's purge of senior defense officials, which has been a months-long trend, tracked closely by global headlines.
In this latest move, first reported internationally by Bloomberg Thursday, the country's top legislative body stripped Ground Force Commander Li Qiaoming and Information Support Force Political Commissar Li Wei of their seats, along with seven other officers.
 Illustrative file image: Reuters
Illustrative file image: Reuters
The dismissals were handed down this week, with state-run Xinhua reporting from the 14th National People's Congress that those targeted include Ground Force's chief Ding Laifu; Central Military Commission officials Bian Ruifeng and Wang Donghai; Navy officers Shen Jinlong and Qin Shengxiang; Air Force's Yu Zhongfu; and Rocket Force's Yang Guang.
State media has not immediately issued details for the dismissals, or specifics on investigations. Back in late January, when Xi's own right-hand military man, Gen. Zhang Youxia - at the time vice chairman of the Central Military Commission - was abruptly removed, the charge was simply "grave violations of discipline and the law."
Such language is often presented in such crackdowns as a euphemism for corruption, which President Xi has in the recent past described as "the biggest threat". But critics as well as Western observers say this has served as a convenient and public PR mechanism for sidelining political rivals, and strengthening Xi's power and hold on the levers of power.
Such is likely also the case with the new firings of these nine military officials. In this fresh case, Beijing has only offered that the officials are suspected of "serious discipline and law violations" - again, just like with the ambiguous Zhang Youxia case.
Xi sent a campaign to eliminate corruption in the armed forces into overdrive around mid-2023, months after securing a precedent-defying third term. Since then, authorities have ousted two vice chairmen of the military commission, three CMC members, a former defense minister, and at least a dozen senior generals who commanded major military units, and possibly many dozens - or perhaps even hundreds - of other officers.
A former CIA analyst who follows Chinese elite politics, Christopher K. Johnson, recently told the NY Times of the ongoing purge trend, "This move is unprecedented in the history of the Chinese military and represents the total annihilation of the high command."
The PLA has seen significant internal turmoil, especially since the Communist Party’s 20th Congress in late 2022. Several top military figures - including Defense Ministers Li Shangfu and Wei Fenghe, and CMC Political Work Department head Miao Hua - have disappeared or been removed, and many more followed.
How Xi's military purges could hamper China's ability to fight
— Taiwan News 247 (@TaiwanNews247) February 26, 2026
Two new studies document the crackdown and raise questions about the People's Liberation Army's ability to carry out large-scale operations, such as a potential assault on Taiwan.https://t.co/NlKJO7iebT
In China, the military is controlled by the Communist Party, not the state, and survival at the top depends on absolute loyalty. Even the most senior and trusted officers are not safe in today's political climate.
Tyler Durden Fri, 02/27/2026 - 02:45Russia’s control over it, whether through Ukraine’s withdrawal or forcible expulsion, is considered to be the basis of the US’ peace plan that the Brits and French are dangerously trying to subvert.
Russia’s Foreign Intelligence Service (SVR) reported on the four-year anniversary of the special operation that the Brits and French are plotting to help Ukraine go nuclear. The alleged plan is to provide it with relevant European components and equipment that would then be misrepresented to the world as proof of a domestically developed nuclear program. They’ll also give it at least one actual warhead and/or materials for a dirty bomb.
The purpose is to give Ukraine an edge over Russia in the negotiations.
Zelensky recently claimed that “Both the Americans and the Russians say that if you want the war to end tomorrow, get out of Donbas”, which he flat-out refuses to do, emboldened as he’s been by European support led first and foremost by the Brits and French.
The first are considered to be the masterminds behind various anti-Russian provocations, including false flag plots that Moscow warned about but which never materialized, while the second has been leading the charge to send NATO troops to Ukraine.
Russia has been tight-lipped about what compromises it might consider in exchange for Ukraine at the very least withdrawing from Donbass due to the confidential nature of the negotiations, but it’s possible that its compliance with this demand could lead to a ceasefire. Zelensky and his top two European backers don’t want that even though the EU’s top diplomat Kaja Kallas claimed, regardless of whether one agrees with her, that “Moscow has failed to achieve any of its strategic objectives” so far.
Therefore, the Brits and French want Ukraine to go nuclear out of desperation to hold onto Donbass at minimum, the Kiev-controlled remainder of which consists of the country’s top military fortifications. They expect that Russia would then agree to a ceasefire along the frontlines if Ukraine obtains nuclear capabilities, even if only a dirty bomb, and threatens to use them if it doesn’t comply. At most, this could also hypothetically be leveraged to get it to withdraw from all the territory that Kiev claims as its own.
The reality is that Russia won’t accept a nuclear-armed Ukraine. Putin alluded to Zelensky’s speech at the 2022 Munich Security Conference in which he threatened to revoke Ukraine’s participation in the 1994 Budapest Memorandum under which it transferred Soviet nukes (that were always under Moscow’s control and never Kiev’s) to Russia in his address to the nation announcing the special operation. Most Russian-friendly observers accordingly expect Russia to not let this happen under any circumstances.
Head of the Duma’s Defense Committee Andrey Kartapolov debunked the scenario of Ukraine developing its own nuclear program in fall 2024 after Zelensky sensationally suggested going down this route if it’s kept out of NATO before walking his words back later that same day. With that in mind, Russia certainly knows that the only way for Ukraine to obtain nukes is from the Brits and/or French, and any attempt to do so would amount to them going behind Trump’s back to subvert his peace plan.
The gist is that Trump reportedly wants Putin to freeze the conflict if Ukraine withdraws from Donbass or is forcibly expelled from there, with the incentive to do so being a resource-centric strategic partnership between Russia and the US. Regardless of whether or not Putin would agree to this, the point is that the Brits and French’s efforts to help Ukraine go nuclear out of desperation to hold onto Donbass undermine the basis of Trump’s peace plan, so he should thus do everything to stop them if he truly wants peace.
Tyler Durden Fri, 02/27/2026 - 02:00Authored by Paul Crespo via RealClearWire,
As many focus on the world’s largest island, Greenland, and President Trump’s aggressive efforts to acquire it, another strategic Arctic island, nearby Svalbard, may be an even more likely future point of contention and conflict.
Not a conflict between the United States and Denmark, or the U.S. and NATO, but between Russia and Norway, and perhaps all of NATO.
Or maybe not with NATO. This is because Svalbard, is not just sovereign territory of Norway, but also has legally established Russian settlements dating back two centuries. And that makes Svalbard uniquely dangerous.
Svalbard, more properly an archipelago, about twice the size of Belgium, with total population of about 2,500, nominally belongs to Norway, but under the terms of the 1920 Svalbard Treaty, certain countries, including the United States, Denmark, China, and Russia have rights of access.
While Norway claims sovereignty, Russia, which has the second largest population on the islands and two long-standing Soviet-era settlements, frequently contests Norway’s claim.
This long-standing presence is one of the main justifications for the Russians laying their own claim to being the second major arbiter of what happens on Svalbard, after Norway.
And China, since 2004, now has a polar research facility, Yellow River Station, with links to its military, on Svalbard, further complicating the strategic equation.
Strategically located just 429 miles east of Greenland at its closest, Svalbard is the northernmost populated land in the world. It lies 404 miles north of the Norwegian mainland and just 621 miles from the North Pole and enjoys ice-free anchorage in the south.
My Visit to SvalbardI visited Svalbard in June and July of 2025 for almost a month, staying in the capital Longyearbyen as well as the two Russian settlements, Barentsburg and Pyramiden. Two years earlier, Tom Cruise filmed parts of his recent film, “Mission Impossible: The Final Reckoning,” on Svalbard.
Just days prior to our visit, Norway’s 88-year-old King Harald and Queen Sonja—as well as Vladimir Putin’s trouble-making Russian Orthodox bishop Vladika Iakov, known for promoting Russian territorial claims in the Arctic—made competing visits to the island at the same time, albeit in different locations.
The Kremlin is using the Orthodox Church as a spiritual weapon to create a narrative that the Arctic belongs to Moscow. In the same vein, King Harald’s visit was also intended to demonstrate that Norway’s sovereignty of Svalbard remains solid.
Russian PresenceToday, the Russian presence is far smaller than during its Soviet-era heyday, when its two coal-mining towns, Barentsburg and Pyramiden, alone had a combined population of almost 2,500—or when Russians outnumbered Norwegians on Svalbard by nearly 2.5 to 1.
Now there are barely 500 Russians there, although their numbers are greatly outsized by their puffed-up presence.
Pyramiden is now a ghost town, boasting the world’s northernmost statue of Lenin, and a treasure trove of Soviet-era artifacts and buildings (with only a skeleton crew of caretakers, usually less than 10), while Barentsburg, still an active mining town (for now), hosts a few hundred Russians.
The Russian flag flies there, and occasionally nostalgic Soviet ones as well, and there is also a Russian Orthodox Church closely tied to Putin’s regime. There is also a heliport at Pyramiden for use by two Russian Mi-8 helicopters on Svalbard.
Barentsburg also hosts a heliport, and the Russian helicopters use the facilities at Longyearbyen Airport in the capital as well.
An unmarked black van driven by a chain-smoking Russian in a black leather mobster jacket quietly picked us up from our hotel in Svalbard’s capital on the way to Pyramiden.
When we arrived at the Russian town of Pyramiden, the hotel staff quickly noted that they already knew who I was. So much for my visit remaining under the radar.
Later, after we visited the old Russian consulate in Barentsburg, painted a mint green, now a museum, the Russian “museum guide” briskly rushed to the new secure Russian consulate just behind the old one, to the left in brick color, likely to file her report on me.
Why Svalbard MattersWhile largely unknown to the general public, Svalbard is critical to global communications as it also hosts the Svalbard Satellite Station (SvalSat), the world’s largest ground-based satellite communication and tracking installation, located on a flat mountain plateau just above the capital town of Longyearbyen.
The site comprises 170 massive radio domes, radomes, containing huge dish antennae to track and communicate with satellites for everything from weather observation, maritime surveillance, navigation, and search and rescue.
In 2021, Russia complained about Norway’s satellite infrastructure, claiming the SvalSat station violated the treaty because it is a “dual-use” facility with potential military uses.
While administered by Norway, Svalbard is a demilitarized territory, The 1920 treaty prohibits the use of the archipelago for “warlike purposes.”
Only a very small Norwegian police force is allowed on the island. It is fully integrated into the Norwegian police system but operates as a specialized district.
The Governor of Svalbard has the same authority as a chief of police on the Norwegian mainland.
Svalbard Is DemilitarizedNorwegian police jurisdiction includes the entire archipelago and its territorial sea focused on environmental crime, search and rescue (SAR), and keeping public order.
However, as of 2026, the police are monitoring increased Russian intelligence activity, espionage, and potential threats to infrastructure in the region.
Of note, when I landed in Svalbard in June, I quickly noticed several fit, Russian-speaking, military-aged men in civilian clothes at the airport, with military style packs and bags. They immediately began scouting around with binoculars.
One can only speculate if they were GRU, Russian military intelligence, or something just as sinister.
Following the letter of the law in the treaty, Norwegian coast guard ships patrol the fiords for months at a time, but don’t dock.
While there, I witnessed a modern Norwegian coast guard ship, the KV Jan Mayen (W310)—the lead ship of the new class of offshore patrol boats—cruising nearby during our entire visit.
Having a lawfully allowed Russian presence on the island and being required by treaty to remain demilitarized, makes Svalbard’s connection to NATO and ensuring it falls under Alliance protection, potentially problematic.
But, just as a look at a polar projection map shows how vital Greenland is to North America, a glance at the map reveals why Svalbard’s location matters to Russia. The Kola peninsula, key to Russia’s nuclear capabilities, is immediately to Svalbard’s southeast.
The Russian ThreatRussia’s growing northern fleet is also based north of Murmansk, and Franz Josef Land archipelago, annexed from Norway by the Soviets in 1926, hosts major Russian military assets, and lies about 250 miles to the east and partly to the north of Svalbard.
Russia constructed a new air base on Franz Josef Land in 2021, publicly justifying it to defend their nuclear weapons on the Kola Peninsula. It uses its base there to threaten the surrounding areas around it, including Svalbard.
As noted by Arctic Today in September 2025:
“Russia has significantly strengthened its military presence at the archipelago. The Nagurskoye base today includes a major building complex, an airfield and powerful arms, including the Bastion system, a Monolit-B coastal radar, as well as anti-drone equipment. In a bid to intimidate Norway and its NATO allies, the Russian war ministry emphasizes that the onyx missiles are ‘almost undetectable’ for modern air defense systems and capable of ‘destroying naval vessels of any size at distances of up to several hundred kilometers.’ ...
“As part of Zapad-2025, Russia this week also conducted mock strikes with its Kinzhal missile over the Barents Sea. Also the coastal missile system Bal has been engaged, according to the Russian armed forces on Telegram.
“Launch of missile Uran from coastal missile complex Bal. Video by Russian armed forces. Large areas in the Barents Sea have been sealed off in connection with the training. Several of the areas are in the Norwegian exclusive economic zone. According to Northern Sentry, a Norwegian account on X with focus on the High North, one of the exercise scenarios of Zapad-2025 is an attack of Svalbard and subsequent occupation of the archipelago.”
Also, during the Zapad-2025 exercise, according to Arctic Today, a key target in the exercise was an imagined enemy flotilla in the Barents Sea.
The scenario included the landing of Russian troops, weapons and armored vehicles from the landing ship Aleksandr Otrakovsky, and the destruction of imagined enemy saboteurs that had infiltrated the archipelago.
Meanwhile, there have been growing tensions between Norway and Russia on Svalbard.
Growing TensionsIn January 2022, one of two key undersea fiber optic cables connecting mainland Norway to Svalbard was damaged in the Greenland Sea. The Svalbard Undersea Cable System is crucial for satellite data. Russian sabotage was suspected though never proven.
Later, in June 2022, a small crisis also highlighted how Russia could easily escalate a local incident into an excuse for military action.
Norway’s Foreign Ministry denied Russian state-owned coal mining company Arktikugol’s request to open a supply route to Barentsburg, citing sanctions on Russia over its invasion of Ukraine. Russia responded quickly.
Norway’s actions, the Russians claimed, “violated the provisions” of the Svalbard Treaty of 1920, which grants citizens of all signatory nations, including Russia, equal access to the archipelago’s resources.
“Following Norway’s actions, the sovereignty of this country over Svalbard is a big question from now on,” Russian Senator Andrei Klishas said.
Norway’s Foreign Minister denied that Oslo had violated the Svalbard Treaty, saying the shipment “has been stopped on the basis of the sanctions that prohibit Russian road transport companies from transporting goods on Norwegian territory.”
The next month, Norway allowed the goods to be shipped to Barentsburg, relieving the immediate tension.
Still, Russia’s recent rhetoric suggests Svalbard may be a growing target in Moscow’s sights.
In 2023 Russian officials ramped things up and skirted the letter of the law of the 1920 treaty by holding a military style parade down the main street in Barentsburg, including flying a helicopter overhead.
The blatantly militarized display created a lot of concern in Norway.
China Also Eyeing SvalbardBut Russia isn’t the only threat to Svalbard. China, now closely allied to Russia, has been showing increasing interest in Svalbard, and the High North in general, calling itself a “near-Arctic” power.
The Chosen recently reported how the Chinese, who have a had a polar research station on the island for 20 years, are aggressively trying to infiltrate Svalbard as well, and how Norway has responded:
“In July 2024, controversy arose when cruise tourists from Shanghai and Hong Kong took photos saluting in military uniforms while waving Chinese flags in front of a granite lion statue at a Chinese base within the Svalbard archipelago. Despite repeated orders from Norway, China has not removed the [two] statue[s].
“Norway has implemented control measures, including prohibiting foreign sales of private property in Svalbard and denying Chinese students permission to study at local universities on security grounds. It has also restricted voting rights previously allowed to foreign residents, permitting them only if they have resided in mainland Norway for over three years. State Secretary Eivind Vad Petersson stated, ‘No country grants voting rights to foreigners. The Svalbard Treaty guarantees ‘equal access’ but not ‘equal rights.’”
Meanwhile, members of the U.S. House Select Committee on the Chinese Communist Party believe the Chinese, who have access to a powerful radar system that monitors space weather and the atmosphere, are performing military research on Svalbard, which is not allowed under the treaty.
According to an online portal, at least three current research projects using data gathered from on Svalbard have been shared with the China Research Institute of Radiowave Propagation, a Chinese defense organization.
So, China is now also showing a growing, likely military, interest in Svalbard, making it part of the new Cold War occurring in the far north. And potentially the next crisis flashpoint in the Arctic.
Tyler Durden Thu, 02/26/2026 - 23:25
Recent comments